Anti Flag
The challenge binary is a 64-bit ELF file format as can be seen below. Also this file is stripped so the debugging symbols will not be present in this file. This will make the analysis a bit harder.
1
2
$ file anti_flag
anti_flag: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=b8de97bc12c627606510140e43fc13e2efffcee5, for GNU/Linux 3.2.0, stripped
On executing the challenge binary, it prints ‘No flag for you :(’.
1
2
$ ./anti_flag
No flag for you :(
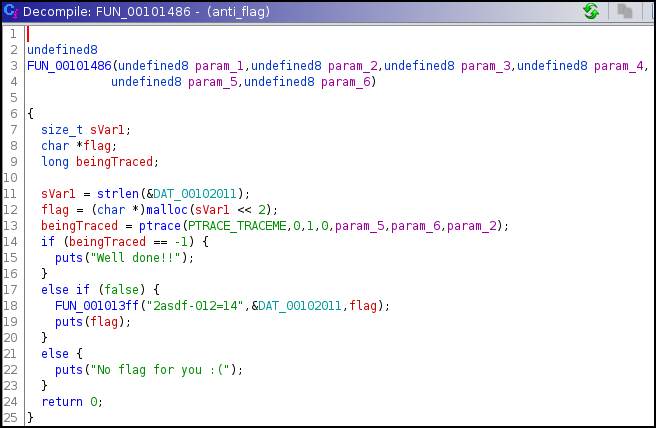
First thing I usually like to do is load the binary in Ghidra. Since this binary is stripped, it might be harder to locate main. The main code is located at FUN_00101486.
- It can be seen that there is call to ptrace, which will checks if the process is being debugged.
- If not found being debugged, it print ‘No flag for you :(’.
- If found being debugged, it should print ‘Well done!!’.
Lets verify.
1
2
3
4
5
6
7
8
$ gdb -q ./anti_flag
Reading symbols from ./anti_flag...
(No debugging symbols found in ./anti_flag)
(gdb) r
Starting program: /home/remnux/HTB/RE/anti_flag
Well done!!
Lets find the execution flow to retrieve the flag.
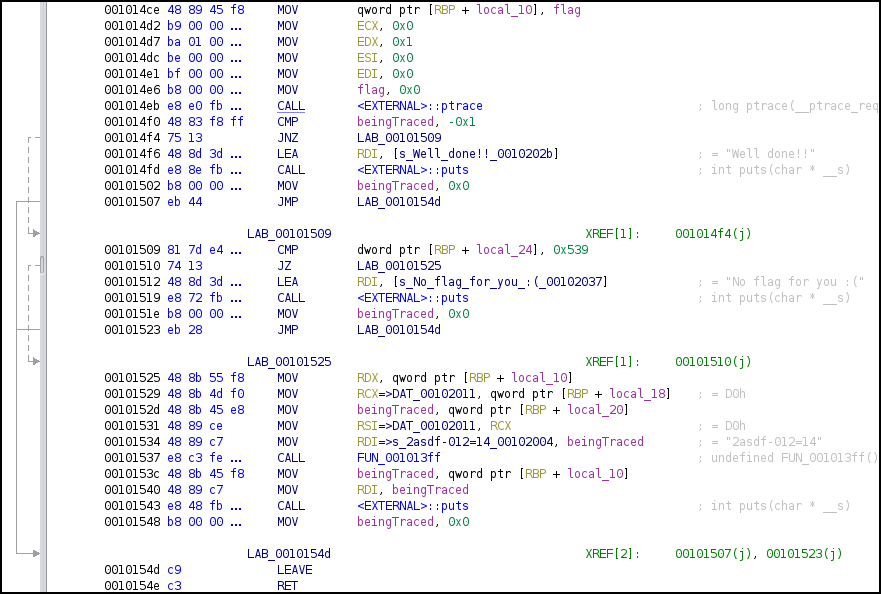
- The program checks if being debugged at offset
0x001014f0with CMP instruction after the call to ptrace. - If found to be debugged, it will not take the jump and prints “Well done!”, then exits.
- If not being debugged, it will take jump to offset
0x00101509. There is yet another CMP instruction, where it is comparing a local variable with 0x539. The local variable is the ‘2asdf-012=14’. So, the program is bound to fail this check so it will not take the jump and prints ‘No flag for you :(’, then exits. - To retrieve the flag, we need to patch this program.
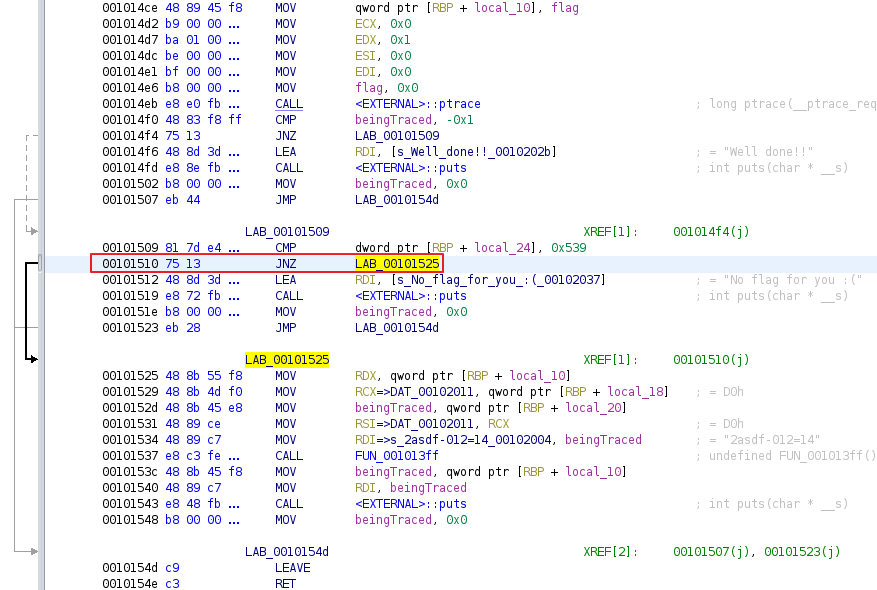
- An easy way is to patch the JZ instruction at offset
0x00101510to JNZ instruction.
- An easy way is to patch the JZ instruction at offset
The program was patched by replacing the JZ instruction at offset 0x00101510 to JNZ instruction as can be seen below. After patching the program, the binary was exported.
Lets now check the patched binary output.
1
2
$ ./patched_anti_flag
HTB{y0u_trac3_m3_g00d!!!}
This post is licensed under CC BY 4.0 by the author.