Challenge 3
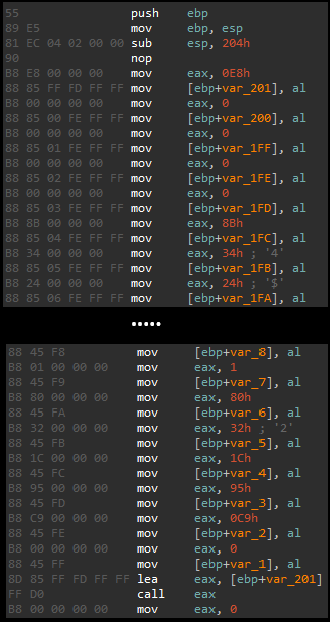
The third challenge was loaded into IDA for analysis and navigated to start > sub_401000. Within sub_401000, an indirect function call was found. Values were sequentially moved into memory locations var_1 through var_201. Ultimately, var_201 contained the code, and its memory address was loaded into the eax register, which was then invoked by a call instruction to execute the code as can be seen below.
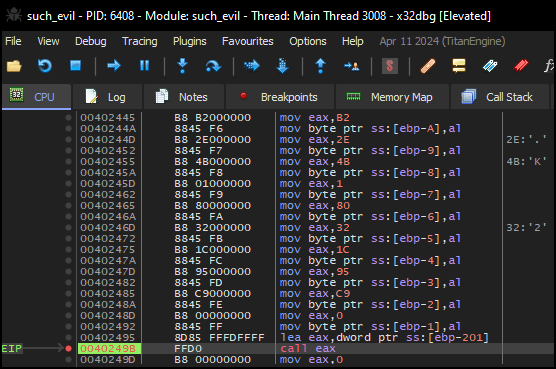
To identify what is being executed when eax is called, the challenge binary was loaded into the x32dbg tool, and a breakpoint was set at the call eax instruction. Then, it was executed until it reached the breakpoint as can be seen below.
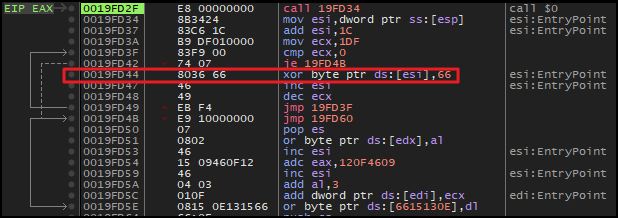
After hitting the breakpoint, it was then stepped into (F7) the code, revealing a decryption routine that contains a loop. In each iteration, the decryption routine performs an XOR operation between 0x66 (key) and a series of bytes, starting at address in esi and incrementing with each iteration.
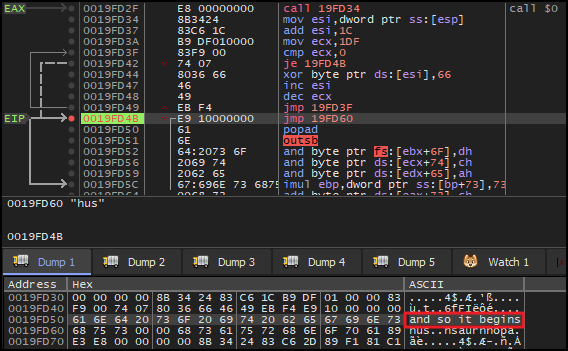
A breakpoint was set outside this loop, and upon execution, the memory dump of address of esi, revealed a readable string and so it begins.
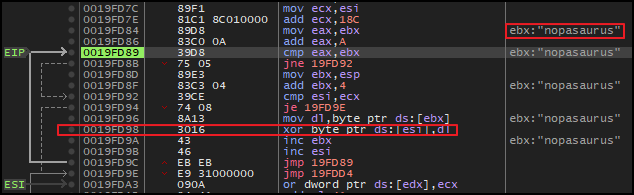
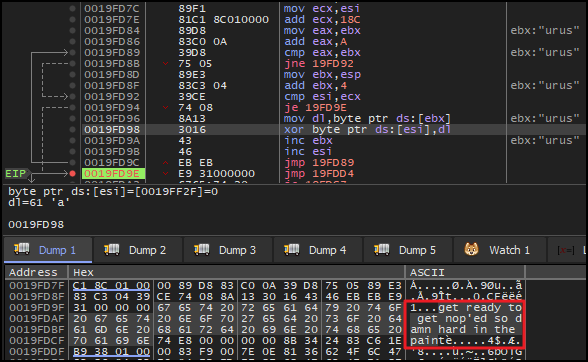
Then after taking the jump and stepping over (F8) couple of instructions, there was another decryption routine that contains a loop. In each iteration, the decryption routine perform XOR operation between nopasaurus (key) and and a series of bytes, starting at address in esi and incrementing with each iteration.
Again, a breakpoint was set outside this loop, and upon execution, the memory dump of address of esi, revealed a readable string get ready to get nop'ed so damn hard in the pain.
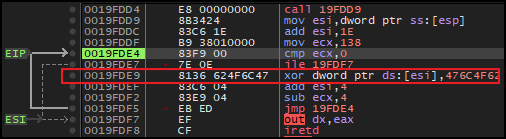
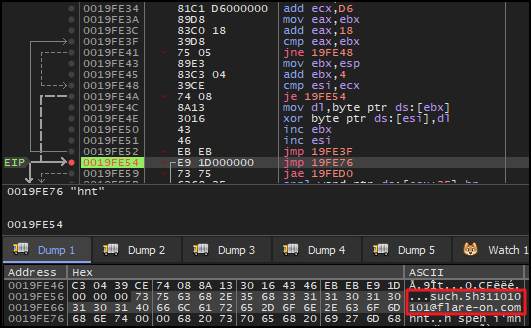
Again, after taking the jump and stepping over couple of instructions, there was another decryption routine that contains a loop. In each iteration, the decryption routine perform XOR operation between 476C4F62 (key) and and a series of bytes, starting at address in esi and incrementing with each iteration.
Before setting the breakpoint outside this loop, make sure to perform one iteration manually. Otherwise it will generate a error. After performing one iteration manually, setup the breakpoint outside the loop. And, upon execution, the memory dump of address of esi, revealed no new visible strings.
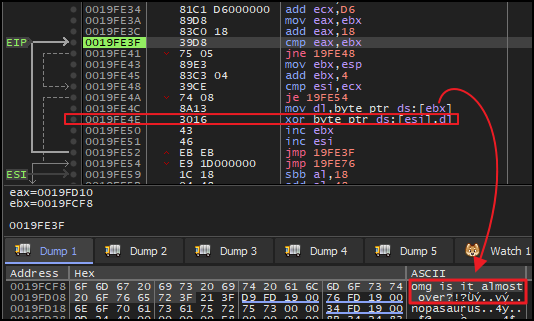
Moving on, stepping over couple of instructions, there was another decryption routine that contains a loop. In each iteration, the decryption routine perform XOR operation between omg is it almost over? (key stored under [edx]) and and a series of bytes, starting at address in esi and incrementing with each iteration.
Again, a breakpoint was set outside this loop. And, upon execution, the memory dump of address of esi, revealed the flag as shown below.
Flag: [email protected]