Challenge 1
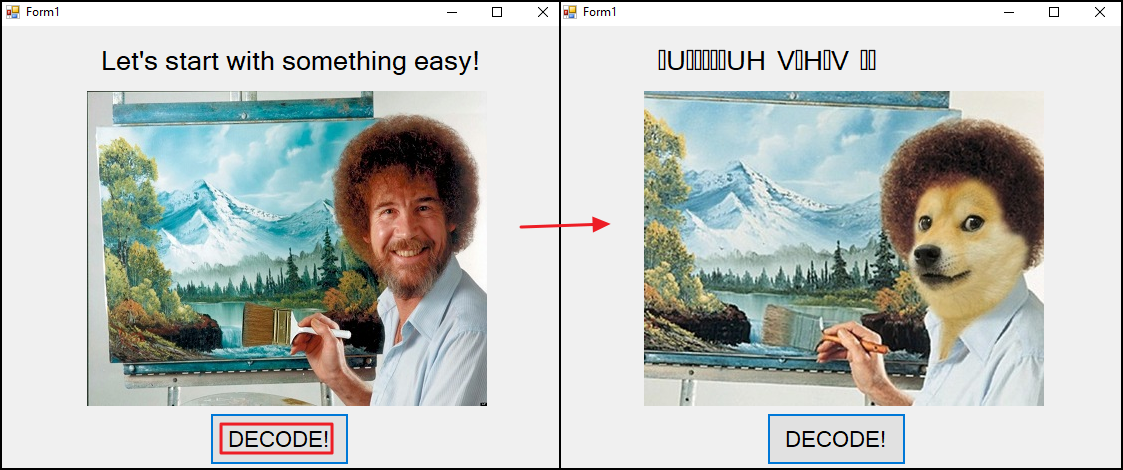
The first challenge binary, Challenge1.exe was executed that displayed the following prompt as shown on the left side. Upon clicking the DECODE! button, the interface changed as shown on right side.
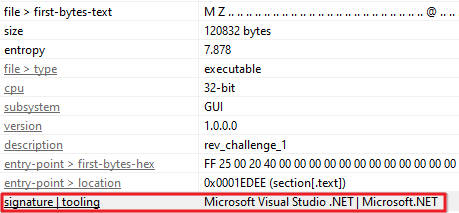
For the initial analysis, the binary was loaded in PeStudio, where it was found that it was developed using the .NET framework.
Given its .NET origin, the binary was subsequently loaded into dnSpy tool for de-compilation. Navigating through the code in dnSpy, the following path was traced: Main() > Form1() > InitializeComponent() > btnDecode_Click()
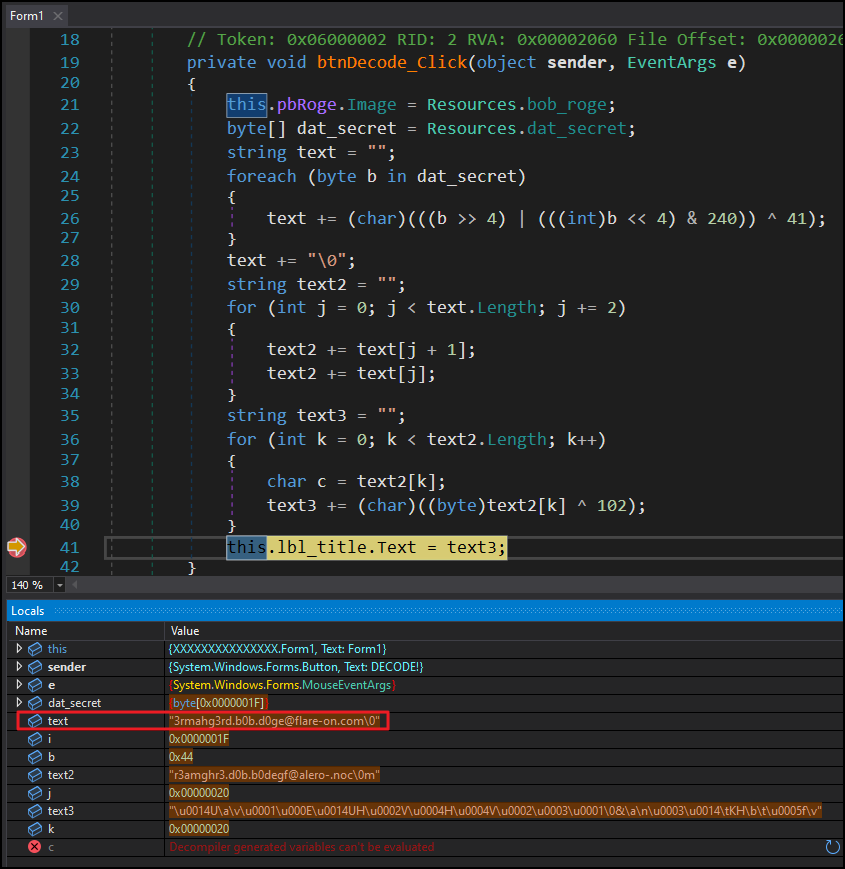
The btnDecode_Click() method contained code that retrieved data from the dat_secret resource and performed some operations on it. To quickly get the final result of these operations, a breakpoint was set at the end of the method. Upon execution, the breakpoint revealed the flag for this challenge as shown below.
Note that the first loop decrypts the flag and stored it in the text variable, while the subsequent two loops appear to be junk code with no meaningful impact. The value stored on text3 is what we seen when clicking the DECODE! button.
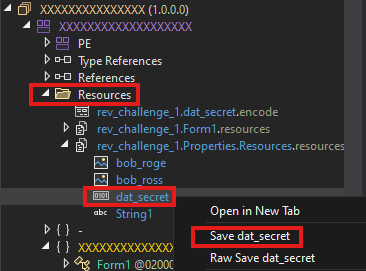
Let’s replicate this process in Python. To begin, we can save the dat_secret resource as:
The saved resource dat_secret content is shown below.
The following Python script decrypts the final flag.
1
2
3
4
5
6
cipher_text = bytes.fromhex("A1B5448414E4A1B5D470B491B470D491E4C496F45484B5C440647470A46444")
plain_text = ""
for text in cipher_text:
plain_text += chr(((text >> 4) | ((text << 4) & 0xF0)) ^ 41)
print(plain_text)
Flag: [email protected]