(I) PE: Overview
Getting Started
A deep understanding of the PE (Portable Executable) file format is fundamental from Windows malware analyst perspective, as it serves as the foundation for analyzing Windows binaries. In this blog series, I will provide an in-depth breakdown of the PE file format, along with some practical tips to help in your malware analysis.
If you want to follow along, the tools that I will be using on this blog series are:
- PE-Bear
- PEview
- CyberChef
Lets now get our hand dirty.
PE Overview
The PE stands for Portable Executable, which is a standard file format for most Windows binaries, including:
- Executables (.exe)
- Dynamic Link Libraries (.dll)
- Screen Saver (.scr)
- Control Panel (.cpl)
- System File (.sys)
- Kernel Driver (.drv)
- Kernel Modules (.srv)
The PE file format is derived from Common Object File Format (COFF). And, the PE file format specifies the necessary information required by OS loader to load the binary in memory and execute it.
PE Structure Overview
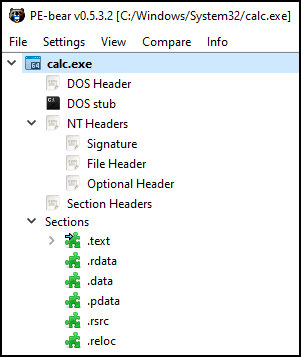
The PE file format is organized as linear steam of data consisting of a header followed by many sections. The PE file format is illustrated in the image below.
This above structure can be seen following in PE-bear tool. Each of those PE structure will be covered in the next section.
PE Structures
Lets now cover each of those PE structures:
PE Header: MS DOS Header, MS DOS Stub & Rich Header
PE Header: NT Header
PE Header: NT Header - Optional Header - Data Directory
PE Header: Section Header & PE Sections
References
PE Format - Win32 apps - Microsoft Learn
2013 Day1P1 Life of Binaries: Intro (youtube.com)
A dive into the PE file format - Introduction - 0xRick’s Blog
Introduction to the PE file format - Cyberdough (skr1x.github.io)
Portable Executable File Format (kowalczyk.info)